analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
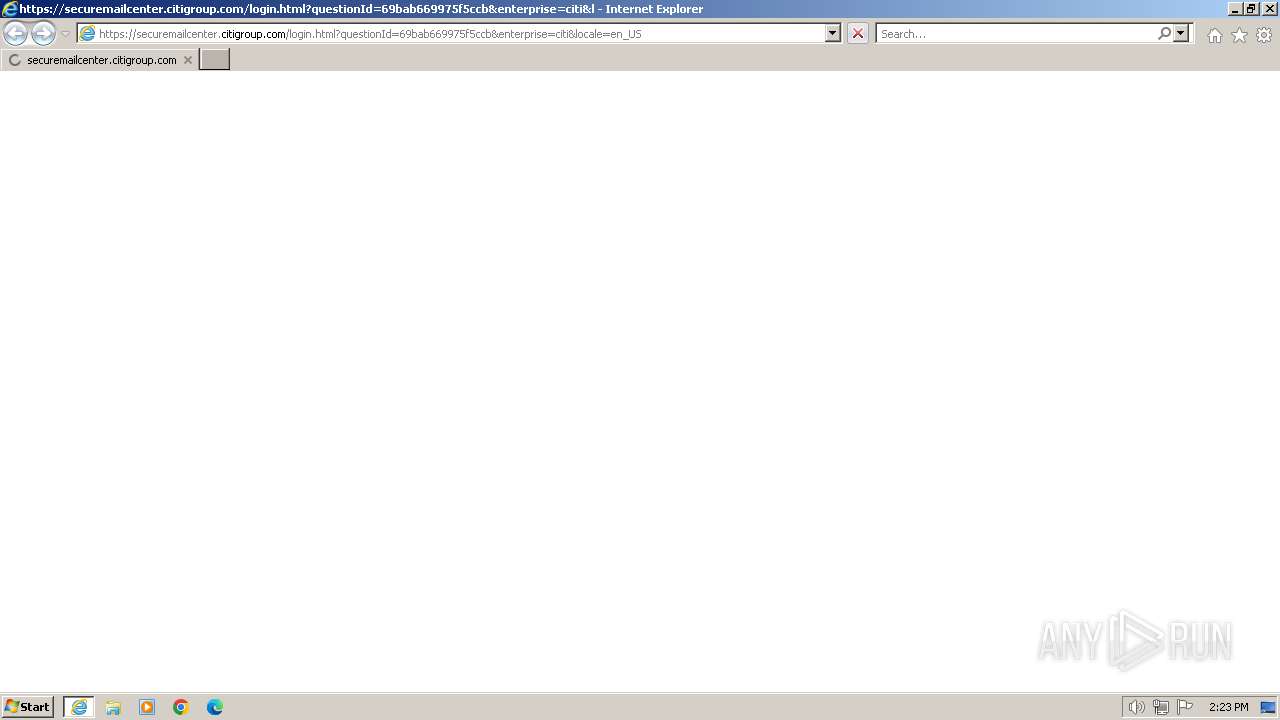
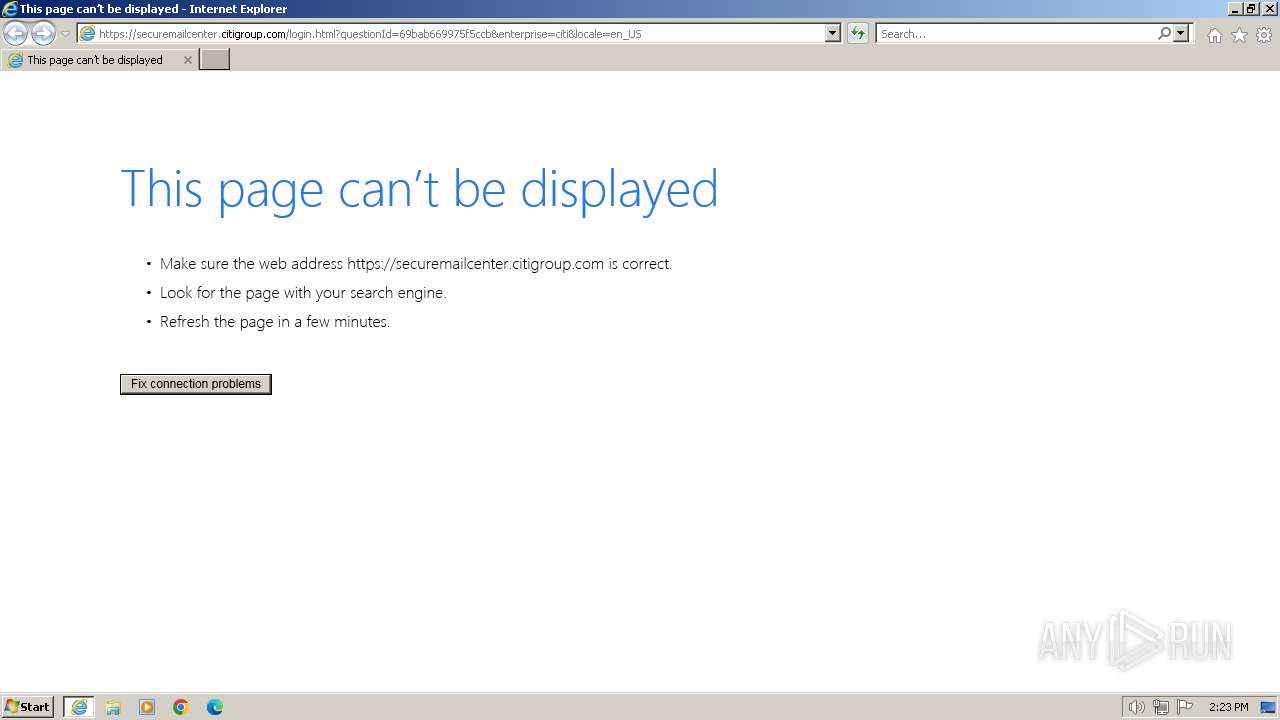
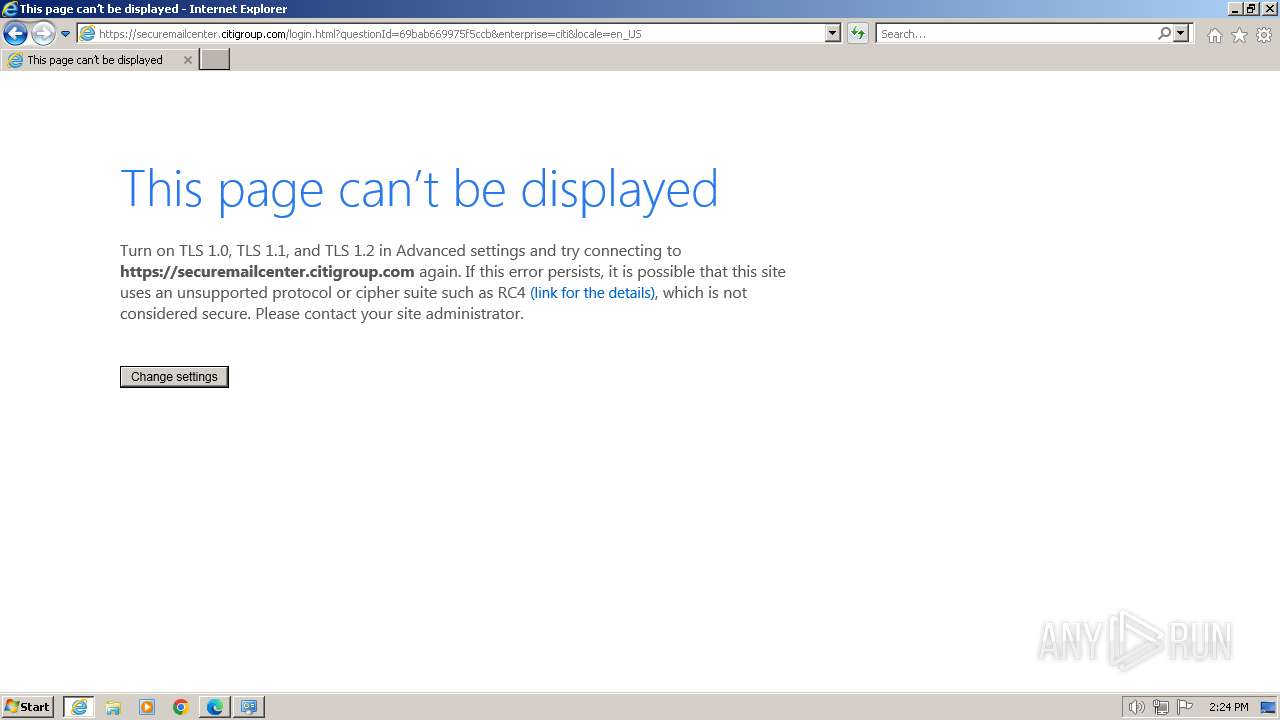
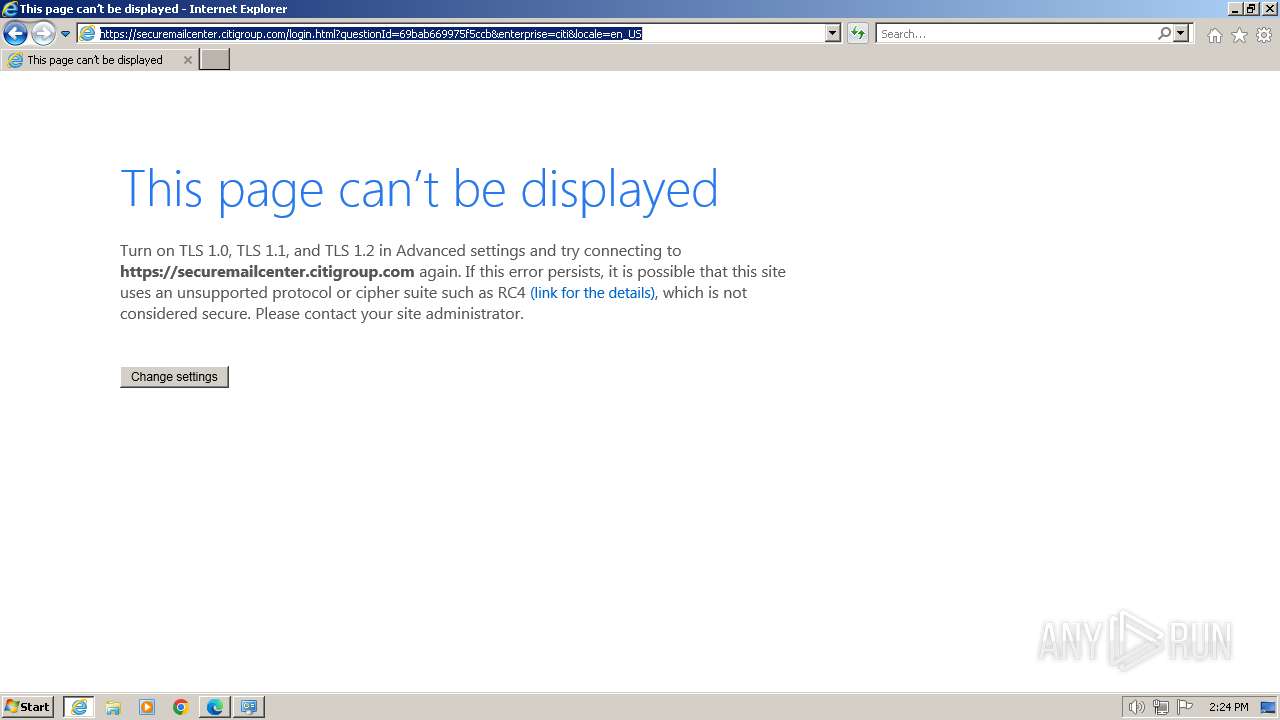
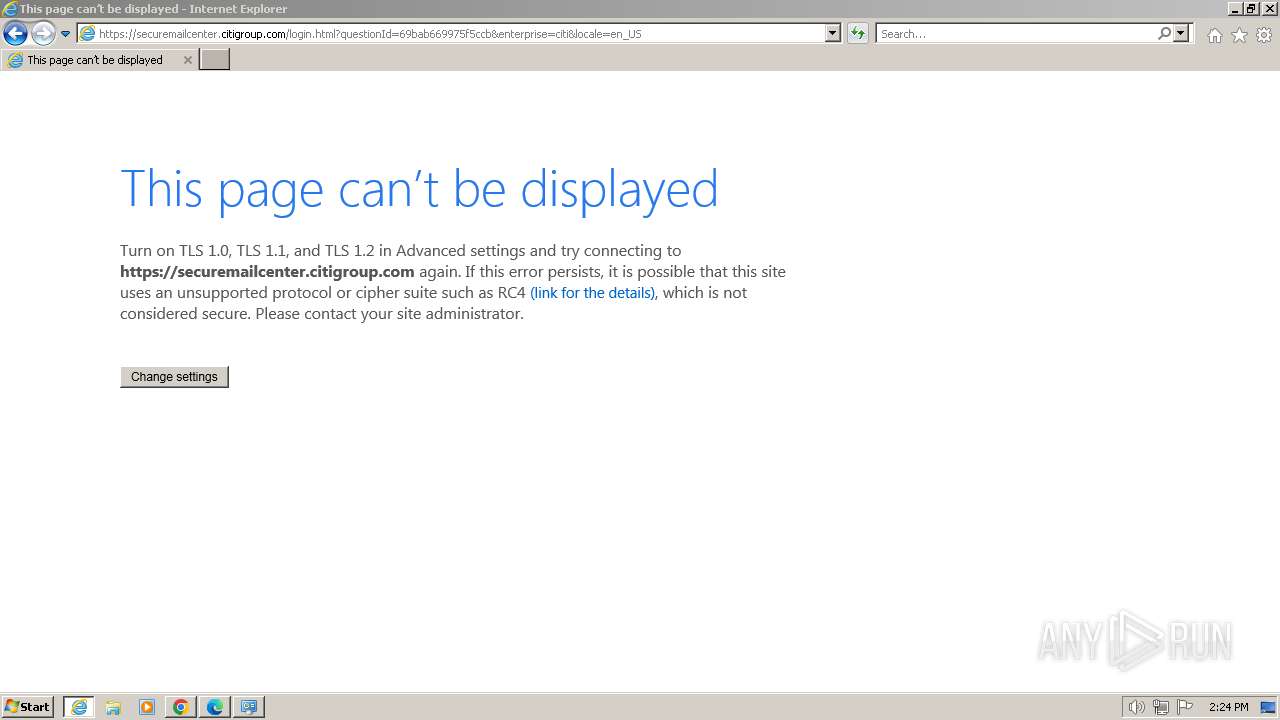
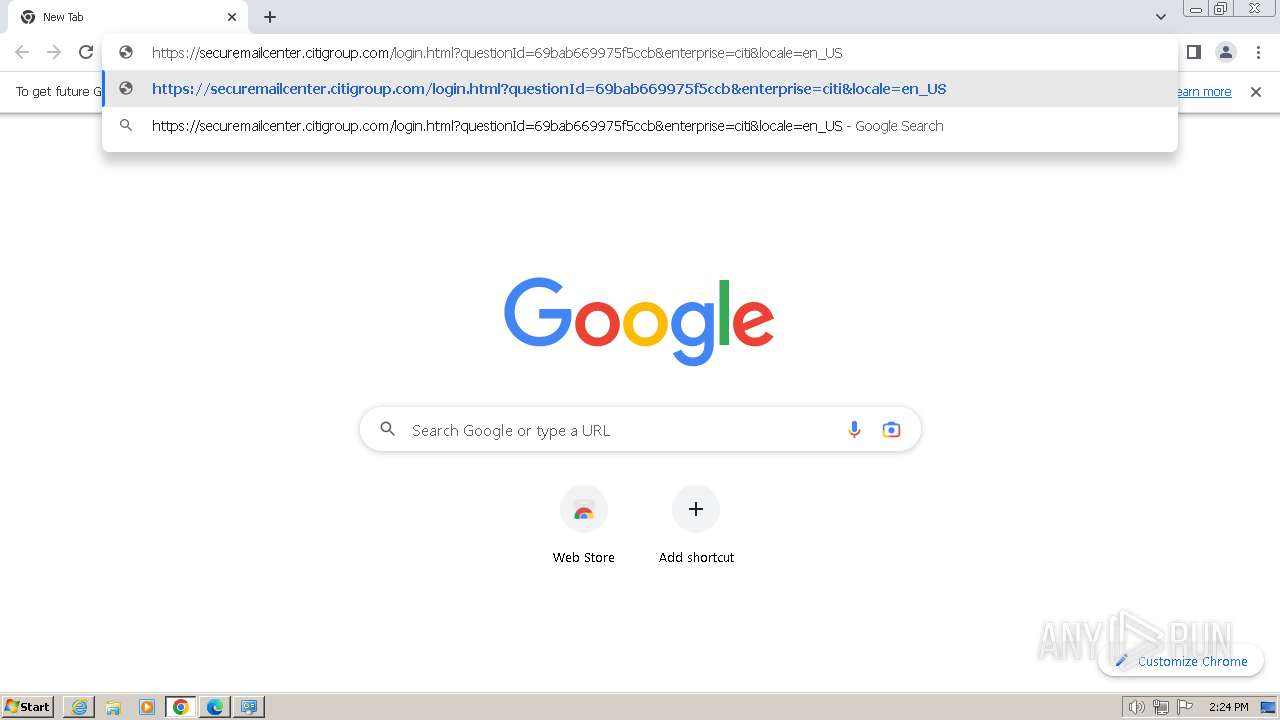
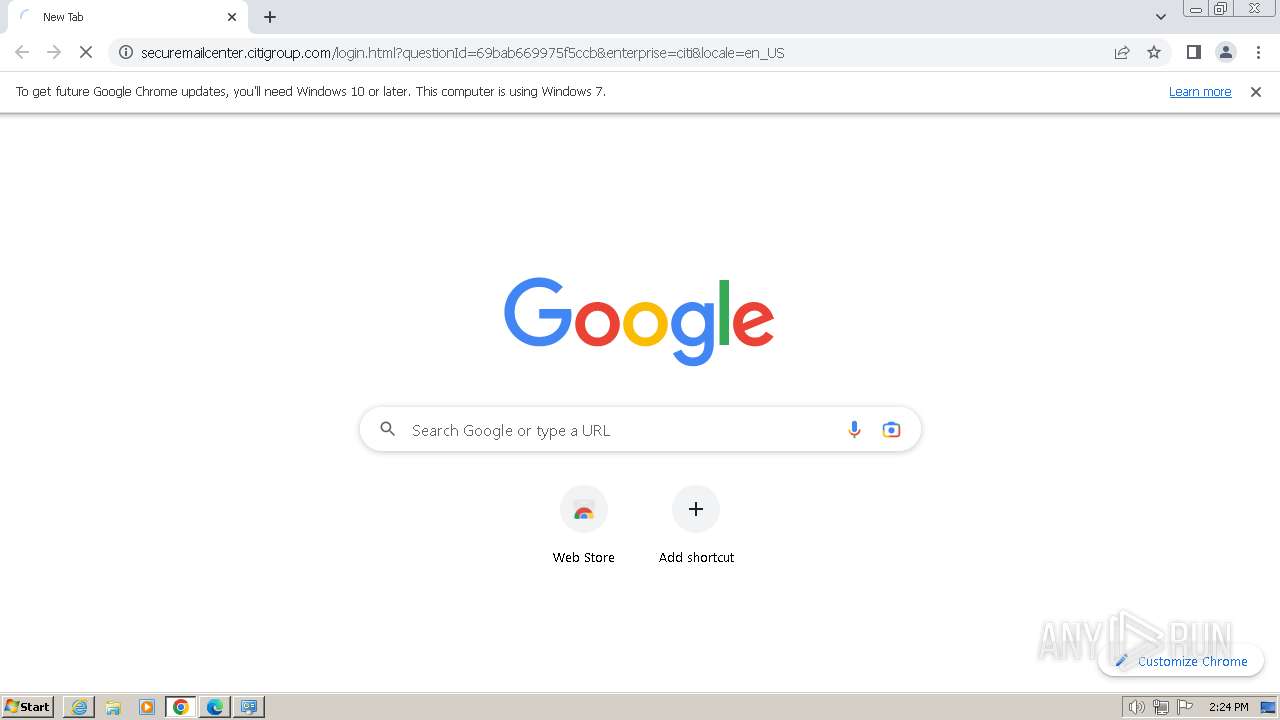
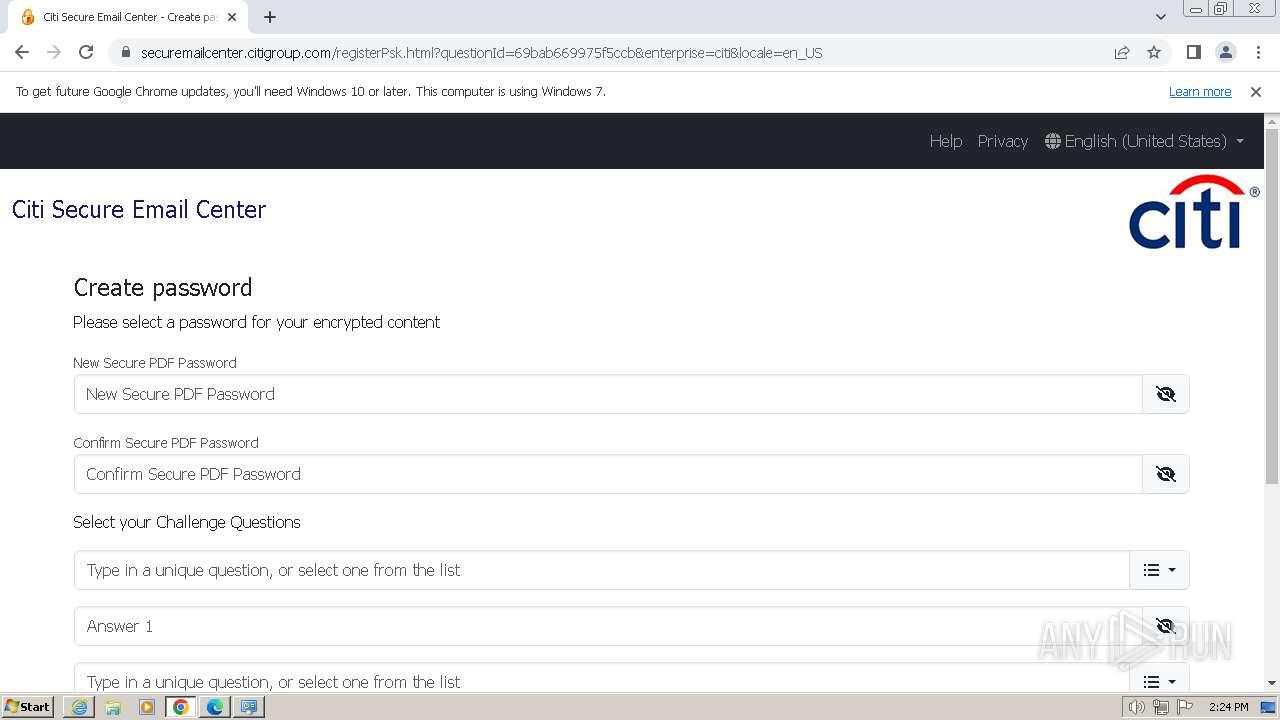
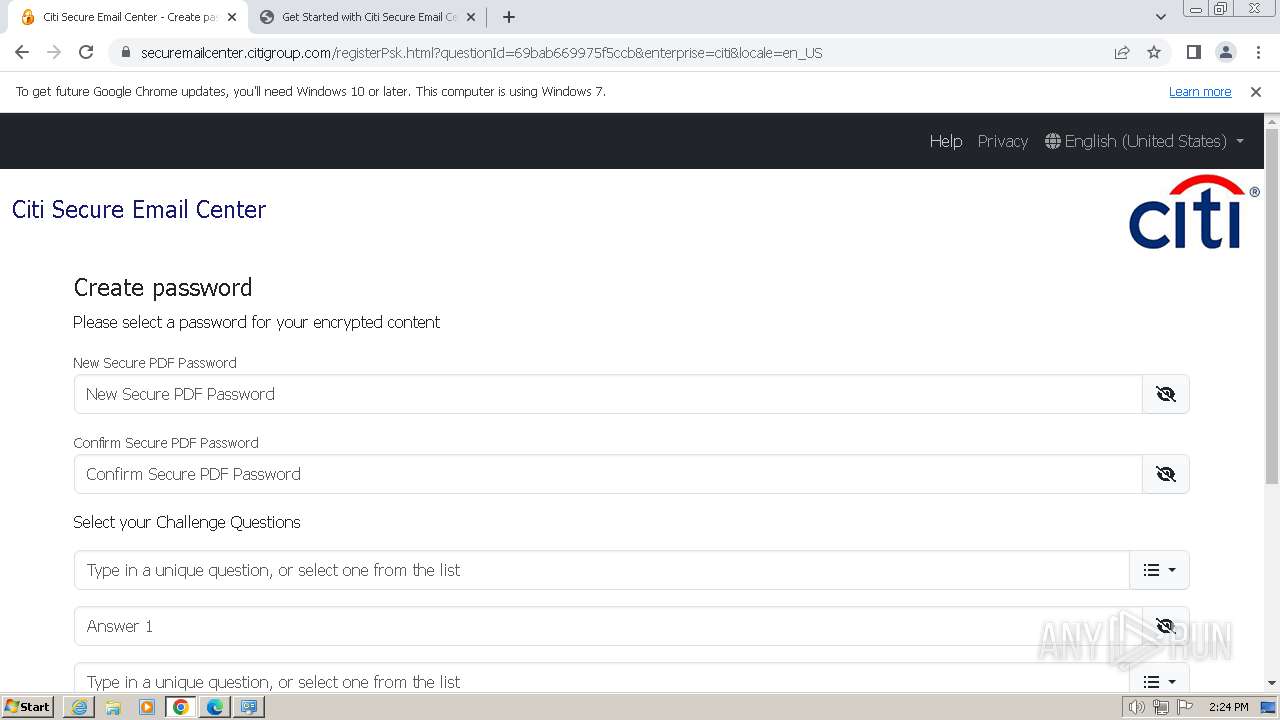
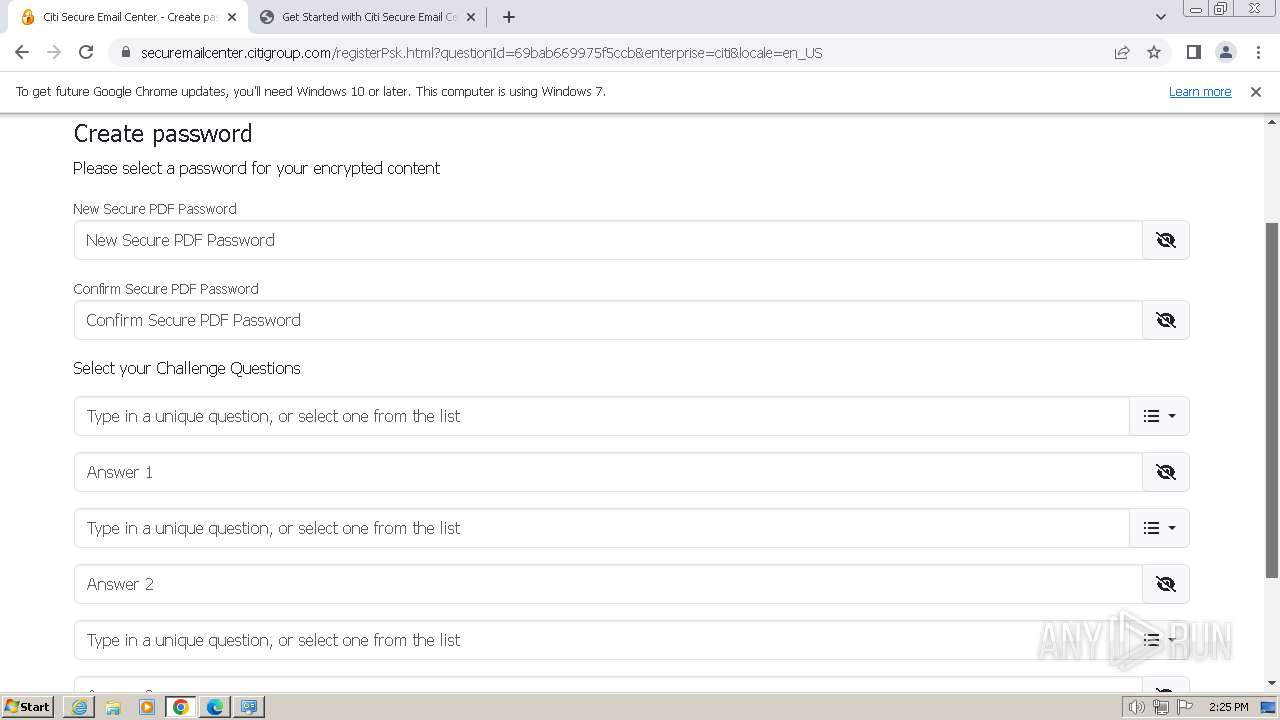
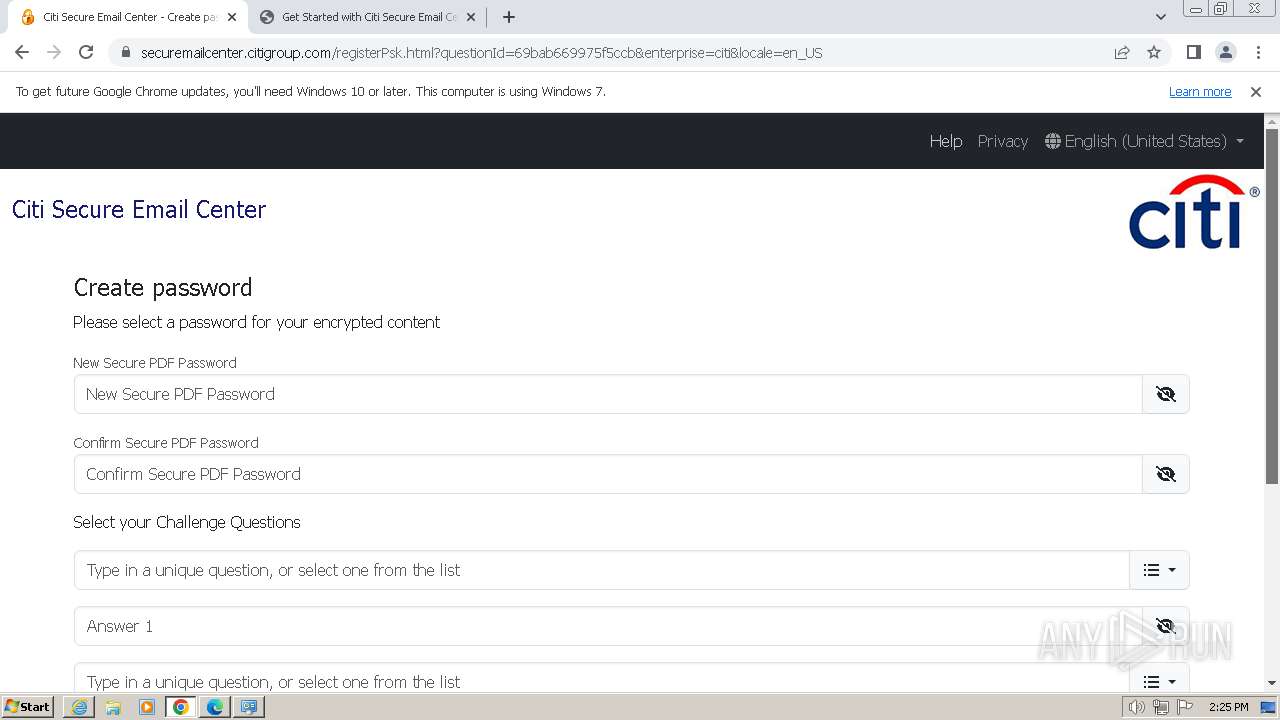
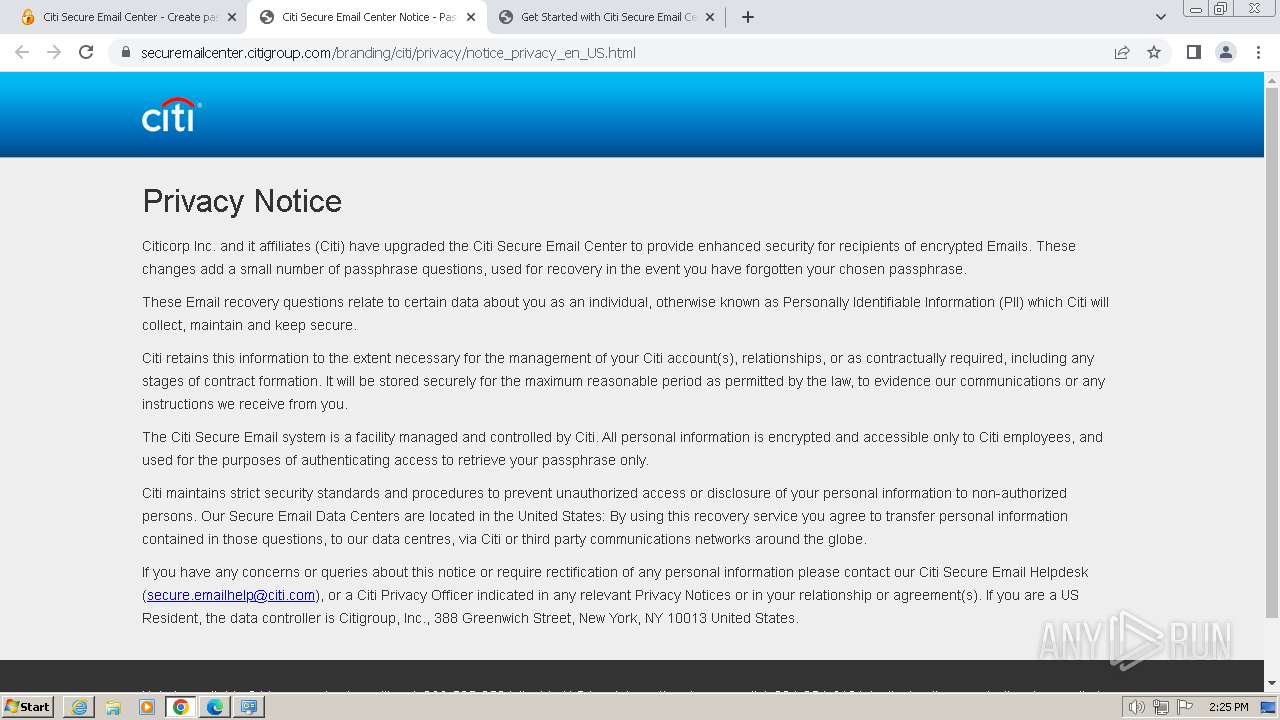
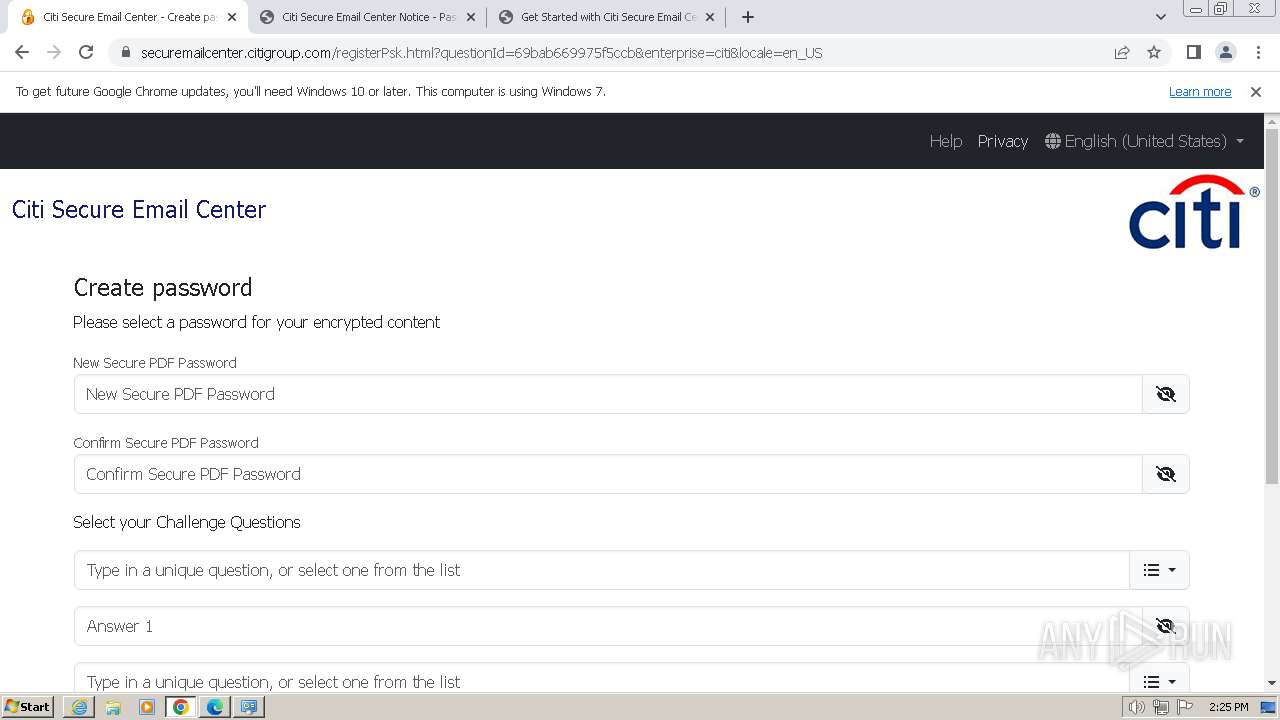
| URL: | https://securemailcenter.citigroup.com/login.html?questionId=69bab669975f5ccb&enterprise=citi&locale=en_US |
| Full analysis: | https://app.any.run/tasks/04d0da10-73ea-46fd-a8ee-58ab84cb10ec |
| Verdict: | Malicious activity |
| Analysis date: | March 27, 2024, 14:23:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 912B83DABEE97377E7B1135373FE7F06 |
| SHA1: | DB5C8EF8BF8D0FEE35D4D26A886E3B7083740B20 |
| SHA256: | E244E2AEDD973AA7FB9BB40237A5BE2FFEC83992528BE96F63A840851A895429 |
| SSDEEP: | 3:N8N3tKuOGMRMCxOCMLPjU8nTckHIQMRjALRyVcWAYRlAe:2ZEDVAPLPjU8TckHtMRjAlyVcWrae |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads settings of System Certificates
- msdt.exe (PID: 3400)
Process drops legitimate windows executable
- msdt.exe (PID: 3400)
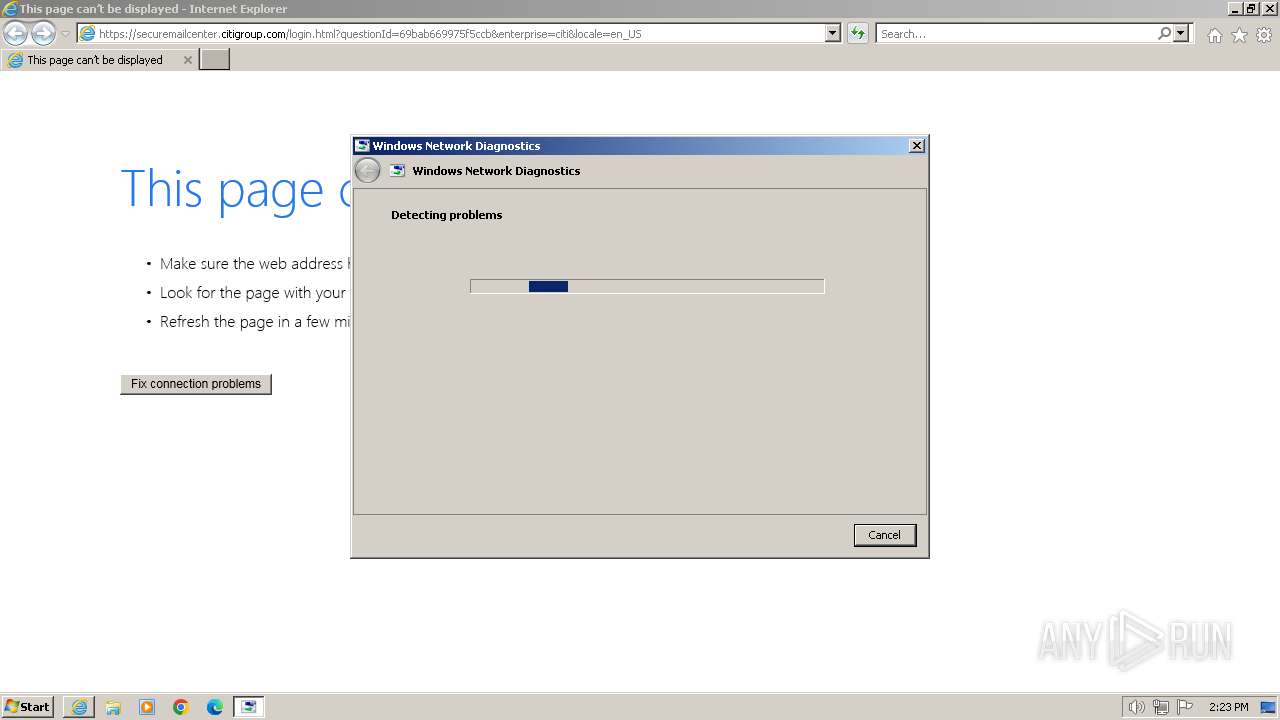
Process uses IPCONFIG to discover network configuration
- sdiagnhost.exe (PID: 1352)
Reads the Internet Settings
- sdiagnhost.exe (PID: 1352)
- msdt.exe (PID: 3400)
Uses ROUTE.EXE to obtain the routing table information
- sdiagnhost.exe (PID: 1352)
INFO
Create files in a temporary directory
- msdt.exe (PID: 3400)
- sdiagnhost.exe (PID: 1352)
- makecab.exe (PID: 712)
Application launched itself
- iexplore.exe (PID: 1696)
- chrome.exe (PID: 3052)
- msedge.exe (PID: 3528)
- chrome.exe (PID: 492)
Drops the executable file immediately after the start
- msdt.exe (PID: 3400)
Reads security settings of Internet Explorer
- msdt.exe (PID: 3400)
- sdiagnhost.exe (PID: 1352)
Reads the software policy settings
- msdt.exe (PID: 3400)
Creates files or folders in the user directory
- msdt.exe (PID: 3400)
Manual execution by a user
- msedge.exe (PID: 3528)
- rundll32.exe (PID: 480)
- chrome.exe (PID: 492)
- chrome.exe (PID: 3052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
92
Monitored processes
54
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1696 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://securemailcenter.citigroup.com/login.html?questionId=69bab669975f5ccb&enterprise=citi&locale=en_US" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4000 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1696 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3400 | -modal 1114548 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF721E.tmp -ep NetworkDiagnosticsWeb | C:\Windows\System32\msdt.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1352 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\System32\ipconfig.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Windows\system32\ROUTE.EXE" print | C:\Windows\System32\ROUTE.EXE | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 712 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\System32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2668 | "C:\Windows\System32\control.exe" /name Microsoft.Troubleshooting /page "resultPage?keywords=+;NetworkDiagnostics" | C:\Windows\System32\control.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | "C:\Windows\System32\rundll32.exe" werconcpl.dll, LaunchErcApp -queuereporting | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3528 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
33 248
Read events
32 961
Write events
246
Delete events
41
Modification events
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31096914 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31096914 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
32
Suspicious files
37
Text files
162
Unknown types
478
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:— | SHA256:— | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:— | SHA256:— | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:— | SHA256:— | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:— | SHA256:— | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[2].ico | image | |
MD5:— | SHA256:— | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\NDF721E.tmp | binary | |
MD5:— | SHA256:— | |||
| 3400 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_71ca8c18-36fd-4b41-8bc0-af59cbfade97\DiagPackage.diagpkg | xml | |
MD5:— | SHA256:— | |||
| 3400 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_71ca8c18-36fd-4b41-8bc0-af59cbfade97\DiagPackage.dll | executable | |
MD5:— | SHA256:— | |||
| 3400 | msdt.exe | C:\Users\admin\AppData\Local\Temp\SDIAG_71ca8c18-36fd-4b41-8bc0-af59cbfade97\HTInteractiveRes.ps1 | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
88
DNS requests
103
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1696 | iexplore.exe | GET | 304 | 23.216.77.53:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?14c8dd88ad9169bd | unknown | — | — | unknown |
1696 | iexplore.exe | GET | 304 | 23.216.77.76:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8a21c6ad756e8dd9 | unknown | — | — | unknown |
1696 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
1696 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 23.216.77.45:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?624d1ab720bef5f8 | unknown | — | — | unknown |
1080 | svchost.exe | GET | 304 | 23.216.77.45:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1dd404ff67a3d8ee | unknown | — | — | unknown |
1696 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | — | — | unknown |
1696 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1696 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | — | — | unknown |
856 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adtp63xadzqu6yysjolme33hjxoq_20220505/dhlpobdgcjafebgbbhjdnapejmpkgiie_20220505_all_adfdqqtvlhuhhtrt6irlkpynghca.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4000 | iexplore.exe | 192.193.154.4:443 | securemailcenter.citigroup.com | SOLANA-CITIPLEX | US | unknown |
1696 | iexplore.exe | 23.53.43.121:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1696 | iexplore.exe | 23.216.77.53:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1696 | iexplore.exe | 23.216.77.76:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1696 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
828 | svchost.exe | 192.193.154.4:443 | securemailcenter.citigroup.com | SOLANA-CITIPLEX | US | unknown |
3172 | msedge.exe | 204.79.197.203:443 | ntp.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
securemailcenter.citigroup.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |