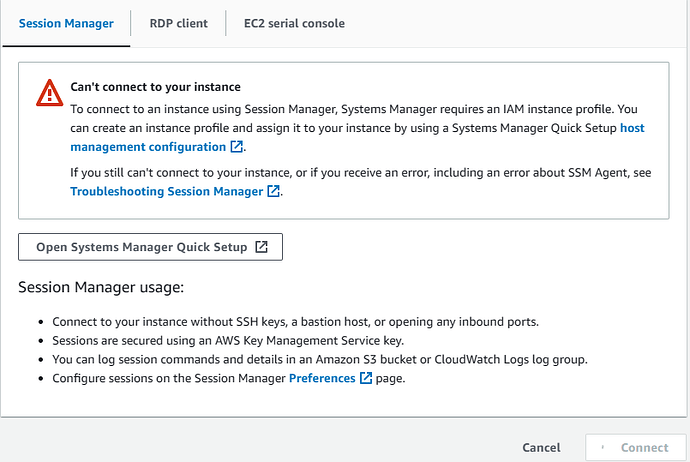
So, for those of you who have dabbled with AWS best practices by not assigning a public IP address (and therefore Internet Access), you are going to run into an issue connecting to your instance via RDP or SSH, as there is no public facing front door.
No biggie - enter the good old Bastion host. Fire up another instance in the console that DOES have access to the internet via a Public IP/NAT Gateway, edit thee needed security groups to allow access from your office, and then securely connect to the non-routable instances from the Bastion host. So, on paper this is fine. But what if you are cheap mofo like me, and don’t want to pay for the instance hours, the public IP address, and management of another box. Enter AWS System Manager Session Manager.
What is session manager? Well direct from the AWS documentation, here is what it says.
Session Manager is a fully managed AWS Systems Manager capability. With Session Manager, you can manage your Amazon Elastic Compute Cloud (Amazon EC2) instances, edge devices, on-premises servers, and virtual machines (VMs). You can use either an interactive one-click browser-based shell or the AWS Command Line Interface (AWS CLI). Session Manager provides secure and auditable node management without the need to open inbound ports, maintain bastion hosts, or manage SSH keys. Session Manager also allows you to comply with corporate policies that require controlled access to managed nodes, strict security practices, and fully auditable logs with node access details, while providing end users with simple one-click cross-platform access to your managed nodes.
Obviously Sessiion Manager can be used for a whole lot more than just connecting to your resrrouces securely. But that is a blog post for another day!
So, when I attempted to connect to my Instance via Session Manager, I got the above ugly error. What’s up with that!
Well, let’s dig in!
The error itself is pretty straightforward, if you understand the various services/tools/technologies that are available.
Long story short, you need to add an IAM (Identity and Access Manager) policy to your EC2 instance. It took some serious Google-Fu to determine what that was, so here I give it to you in black and white.
AmazonSSMManagedInstanceCore
Assign this policy to your EC2 instances, and wait.
And wait.
Then reboot.
Then wait.
Wait a little more.
For some reason, it takes an eon for these permissions to apply. In my case, it took a good 30 seconds before the permissions updated on the EC2 instances, and I could click connect within Session Manager.
Oh - as an aside. If you plan to connect to Windows using Session Manager, be warned, the access you get is CLI, something similar to Windows Server Core. This is not RDP.
As always, let me know if you have questions comments in the comments.