The SLocker Android ransomware is back with a new wave of infections, after previously wreaking havoc in the summer of 2016.
This recent wave of infections was spotted by security firm Wandera, who reported yesterday about a new wave of infections that targeted users towards the start of the year.
The company says it identified these new infections, who were previously largely undetected and unreported, after using a new machine learning system to detect similarities between older SLocker versions and other suspicious apps.
Over 400 new SLocker variants discovered
This helped the company identify over 400 new SLocker variants that featured small changes here and there, which allowed them to pass undetected by most mobile security apps.
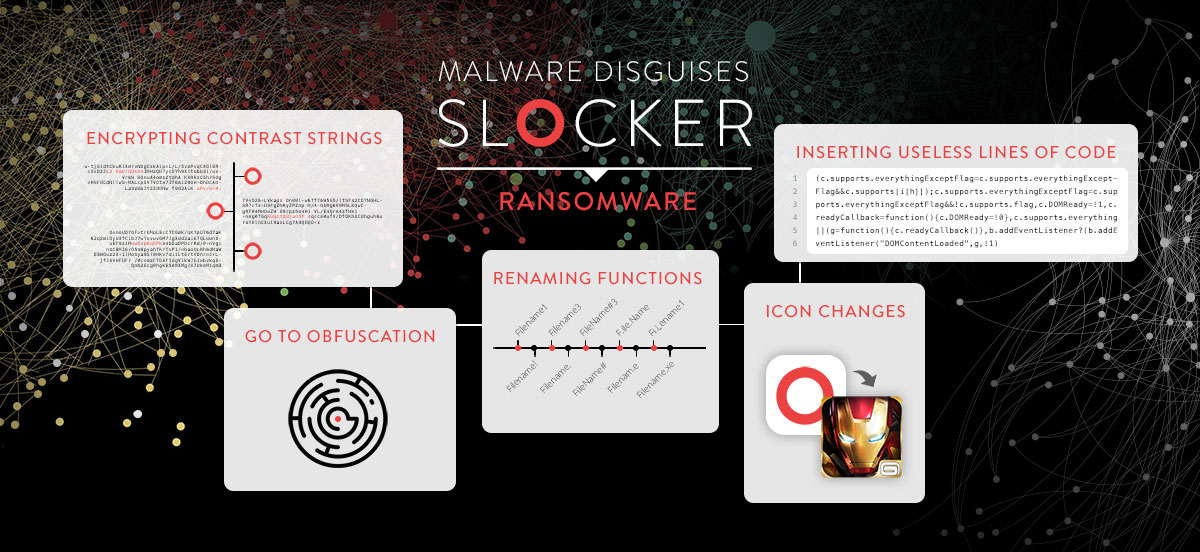
These changes included the usage of new icons, renamed source code functions, heavy obfuscation, and the insertion of dummy code inside the app to alter its structure.
With these new 400 variants, this brings the total number of SLocker variations to over 3,000.
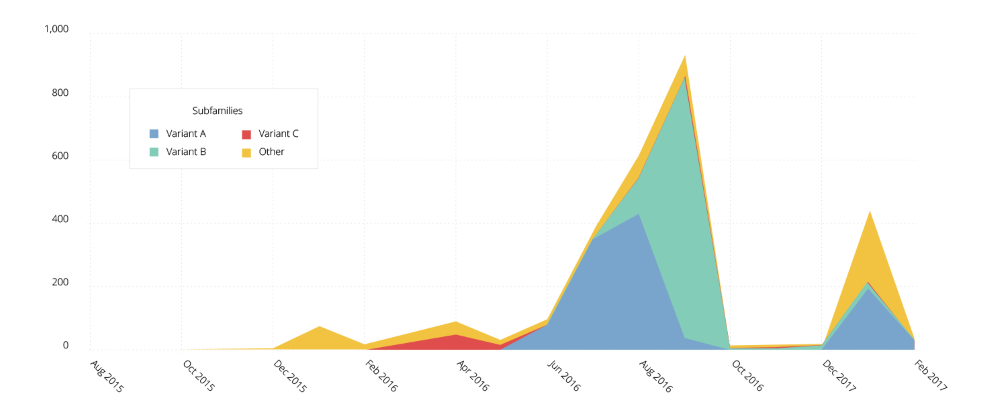
The SLocker ransomware is one of the most aggressive Android ransomware strains known today. This threat appeared in August 2016, when it made a large number of victims among SMB companies. A report estimated that the SLocker creators made tens of millions just for the August 2016 operations.
Under the hood, the ransomware works just like other threats. After the user installs a tainted app, SLocker starts a hidden process that starts encrypting the user's files.
Once the encryption process ends, the ransomware locks the user's device and shows a ransom note, which usually tries to shame victims into paying, using the classic theme of "Police has caught you watching forbidden adult content."
Some of the features that made SLocker stand out was that it used Tor for the C&C server communications and that it was one of the very few Android ransomware families that actually encrypted data. Most Android ransomware just restricts access to your screen, but rarely encrypts any files.
Since August 2016, the SLocker ransomware was spotted in two high-profile incidents. In early March, Check Point researchers found the SLocker ransomware pre-installed on 38 high-end devices belonging to two multinational companies, and in late March, Zscaler experts found an SLocker variant that was capable of avoiding all mobile antivirus apps, which in hindsight, is consistent with Wandera's most recent report.
Image credits: Wandera
.jpg)

Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now