Building Control System Network Configurations - Perception vs Reality
What IT and Facility Management think is reality and what the reality actually is
Most building control system (BCS) operational technology (OT) networks do not have IT involvement. For the ones that do, IT either knows they don't know what is there or the more dangerous situation, they think they know what is there and think they are effectively managing it. I acknowledge there are IT departments that do but the majority do not fully understand and manage BCS OT networks.
Examples of BCS OT Networks
The following high-level diagrams show what we see on a regular basis and hopefully get a discussion started in your organization to really take time to find out how your BCS OT networks are configured. And the good news is there is a way to do this without major disruption or cost.
Example 1 - IT has a switch and server that it manages but does not "see" anything beyond the server. The belief is that by keeping the switch and server up-to-date security is maintained. The reality is no one knows or manages, except maybe the system vendor, what is beyond the server OS and AV/AM and therefore there are still breach points. The building control application on the server is not maintained by IT and is only maintained by the OT vendor when requested and for the most part, the applications on the server and the supervisory controllers are the same as when they were first set up. The same is true for the field level controllers.
Example 2 - This one happens a lot. IT has a switch and server that they manage but they do not "see" anything beyond the server. The OT vendor had either a DLS or cellular modem and uses on a cloud solution such as TeamViewer or LogMeIn to remotely access the system. The facility staff uses it too. The OT vendor controls access and has 24/7 access to the system. IT has no idea this access has been set up. And as an added kicker... The OT vendor has a shared user account for all of their employees for not only this system but every system they maintain. The same is typically true for facility staff. The user and password are never changed and therefore former employees still have access to the system.
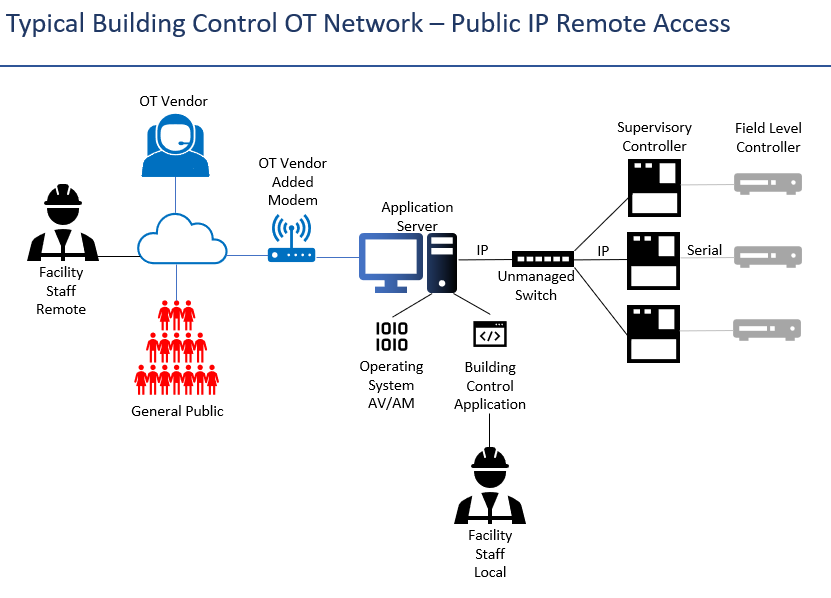
Example 3 - An oldie but a goodie... Public IP access. Regardless of whether IT has access to the application server or not, the OT vendor (and sometimes in the past, IT have even done this) has added a public IP. If you don't know, a public IP is an IP address that anyone in the world can access. OT search engines (Shodan, Censys, ZoomEye) HAVE found you and this IP is and the information about the system (version, location, internal IPs, etc.) is cataloged for anyone to look up. The only thing that stands between an attacker and the getting into the system is the credentials in the application. If the accounts have been set up like most are, a password cracker can eventually get in.
(Note: The above list is not a complete list of building control network configurations)
Chain of Custody
IT and facility staff need to understand how systems are configured and how to effectively manage them. Time and again I have had IT tell me that they are completely in control of the network. They are monitoring the switches, application server, and even the supervisory controllers. The reality is some of the things they miss are:
- Application on the server and the users associated with the application
- Unmanaged switches throughout the building
- Application and operating system on the supervisory controller
- Field level controllers
The reality is IT might be managing the managed switches and the operating system but the OT vendor is in control of the remainder of the devices, applications, and the networks. Even with this, the vendor may not know everything that is connected and how everything is configured.
In summary best practice is you have to know what is connected to your building control network and how they are configured and managed. The best approach is to drop all preconceived notions that the control system is being managed and take a step back and genuinely assess your building control system. And be willing to admit what you don't know and bring in the people that do know.
As mentioned earlier there are ways to do this without major disruption or cost. Intelligent Buildings has created processes and technology that provide a secure path that maintains the building control system network and by providing the solution at an affordable price point.





CEO & founder @Wattsense | Keep control of buildings with a simple BMS
3yThanks Fred Gordy for this great article. As a cloud service provider, Wattsense is asked everyday to prove the security of its system (which is a very legitimate request) while we see so many traditional BCSs that are obviously insecure. I think it goes along with your message, the most risky is what people assume as being under control while they did not check.
Co-Founder & CEO @ SecurityGate | Industrial Risk Management
3ygreat overview here. Definitely following Fred Gordy from this point forward. Mick Vaughan and Brent Gage and Cherise Esparza check it out.
I share OT, IT, and CISO helpful Cyber Content. | Connector | Business Development Expert #Wicys Ambassador #IoTSF Houston Chapter Program Manager Cloud, Network, Communications & MSSP Solutions, OT, IT, IoT Expert
3yHello Fred, We have all heard of cyber attacks moving from IT to OT. In some cases an OT facility may be down for a day or in other cases it can be a lot worse. At SecurityGate.io we bring OT & IT together to help companies determine the entities and locations with the highest risk based on cyber assessments completed. I would be happy to connect and have a conversation.
Building Technology Strategy and Implementation for Owners and Occupiers
3yGreat piece and highlights some of the challenges when it comes to determining risk and attribution. Unfortunately many clients only start thinking about this after a security issue as the perception seems to be that its "out of sight, out of mind," or too expensive/ complicated to delve into. More recent solutions coming on to the market make this far less cumbersome to address properly than even five years ago, so it should be on every building operator's radar sooner rather than later.
Information Security | Tech Developer | IOT Enthusiast | Zero Trust Data Connectivity | Remote Access | Entrepreneur
3yGreat article and documentation of the different outlooks on BMS, we deal with this every day and have solved 100 000's of cases and networks not only to create remote access, but also provide that OT Network of connectivity. The best laugh of it all is when clients see how easy it is to use and manage, they can't actually believe it! If anyone is interested in removing the complexity and being able to secure connections between users, cloud/server and BMS/Edge, DM me and we can schedule a session together!