Complexities of AWS Security Groups in the Cloud World
Do you feel AWS security groups are hard to implement? Are you tired of reconfiguring IP addresses in security groups whenever workloads get restarted or redeployed? You are not alone.
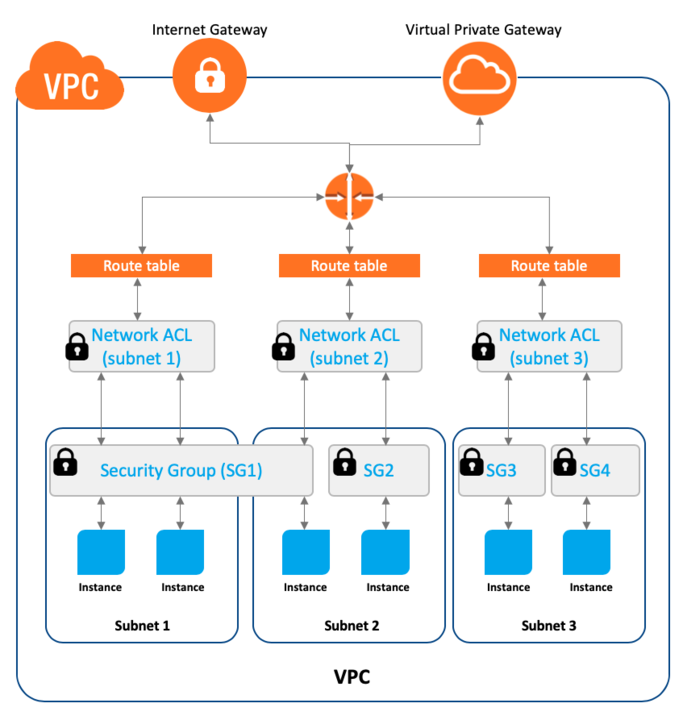
Problems with AWS security groups include:
- Policies are based on a whitelist model. If the policies are too tight applications break, but if policies are too loose security risk increases.
- Policies are stateful and configured based on IP, port, and protocol (both ingress and egress). This makes it cumbersome, especially in cloud-native deployments where workloads are voluminous and app changes are frequent.
- Policies get stale over time and clean-ups require a lot of effort. Sometimes policies are kept wide to avoid frequent updating, for example, the egress is wide open (see below)

Do you think you have a good AWS posture?
Do you think you have tight controls?
Because it's always better to understand your security holes before your adversaries
What if you could
- Auto-discover a Golden Reference to manage your security groups and IAMs.
- Continuous Monitor for Backdoors and get real-time Alerts on any new egress connection.
- Lowers the total cost of ownership (TCO) of writing and maintaining policies while tightening your security posture.
We have been thinking a lot about this problem: