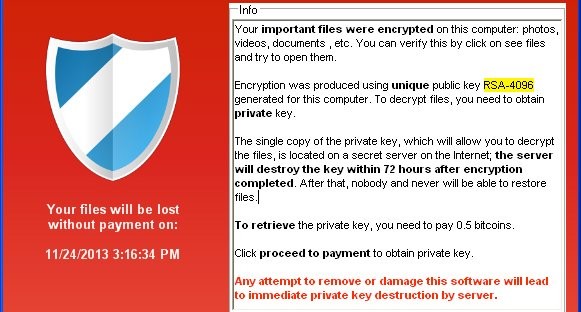
Surviving a Crypto-Virus attack
If you’ve been following the news recently you’ve probably heard of a new and particularly dangerous form of virus currently doing the rounds – loosely termed Ransomware. The term covers a variety of viruses – Cryptolocker, Paycrypt and Locky to name but three known ones, that encrypt businesses’ information and demand a ransom for a decryption key. The ransom is typically payable in Bitcoin – which is worldwide, untraceable and can be converted back to cash by it’s recipient. Unfortunately, though, even if the ransom is paid, you have no guarantee that you will be provided with the key.
At Invistech, we have seen Ransomware viruses infect computers and networks from a variety of sources. We have seen computers and networks infected via e-mail, through normal web usage and in one instance through deliberate infection of a server.E-mail infections generally rely on a user opening an infected attachment (typically a macro enabled document or executable .zip file). Many such e-mails are extremely well-written and convincing, and may have words or phrases specific to the target – for example invoice.pdf or defence.zip. Web infections are facilitated by PC’s with out of date browsers or third party plugins like Adobe Flash or Java. You could visit a perfectly normal and legitimate website using an advertising network that has been compromised and get infected, as we saw in one case where an out of date Flash Plugin facilitated the infection.
Can I stop or avoid this happening?
In short, no. Unless you can disconnect your computers and servers completely from the internet and lock them in a safe to which nobody has a key (not the most practical of solution). Computers and networks will always be vulnerable to a greater or lesser extent.
Can I reduce my risk of being infected? Absolutely. Up to date Anti-Virus on all PC’s and Servers is critically important. Hosted Anti-Virus and Anti-Spam scanning e-mails before they enter your network will block most e-mail infections. Web filtering (similar to e-mail filtering – web traffic is scanned for malicious content and known compromised web sites are blocked) can also help protect from web based threats. A good firewall is an essential element of a properly secured network. Access to local services from the internet if deemed necessary, should be strictly controlled and ideally should also be monitored. Keep in mind that antivirus companies will always be one step behind those that create malware. Recent changes to antivirus software have begun to filter out Crypto-Viruses, but there is always a new threat out there waiting to strike. Keeping your security layers updated will go a long way toward heading off infections before they happen, as will increased vigilance by your employees.
How can Invistech help?
In all the instances of Invistech clients being infected with Ransomware, none have lost more than a few hours’ worth of work. How is this?
Contact me at Killian.Murphy@invistech.com for details on how we can easily protect your business from such attacks.