GA (Domain Generation Algorithm) malware is a type of malware that uses an algorithm to generate a large number of seemingly random domain names. The primary purpose of these generated domain names is to establish communication with Command and Control (C2) servers while making it difficult for security defenders to predict or block these connections. Detecting DGA malware in a security operations center (SOC) involves understanding how it works and employing various detection techniques:
How DGA Malware Works:
- Algorithm: DGA malware contains an algorithm that generates a list of domain names based on various parameters, such as date, time, and a unique seed value embedded within the malware. This algorithm is designed to produce a large number of domain names that appear random.
- Domain Generation: At regular intervals, the malware executes the DGA algorithm to generate a set of domain names. These domains are often constructed in a way that mimics legitimate domain names, which can make them look less suspicious.
- Communication: The malware attempts to contact these generated domains in search of a C2 server. If a C2 server is available and the domain is registered or resolves to an IP address controlled by the attacker, the malware establishes a connection, enabling data exfiltration or receiving commands.
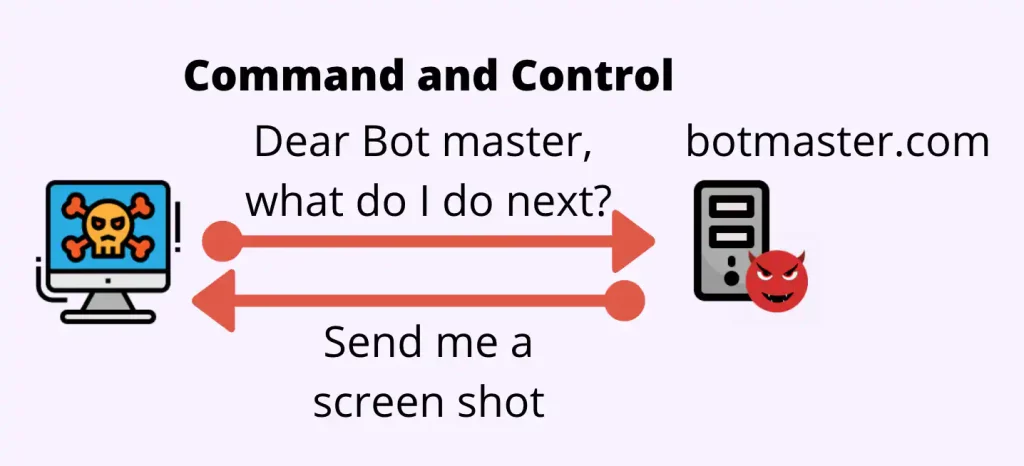
Image Source: https://www.akamai.com
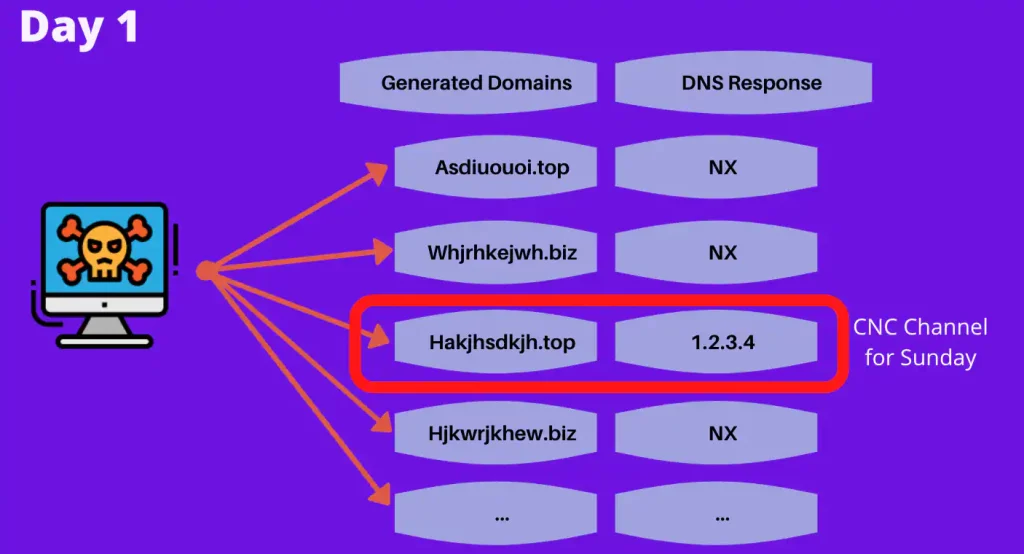
Image Source: https://www.akamai.com
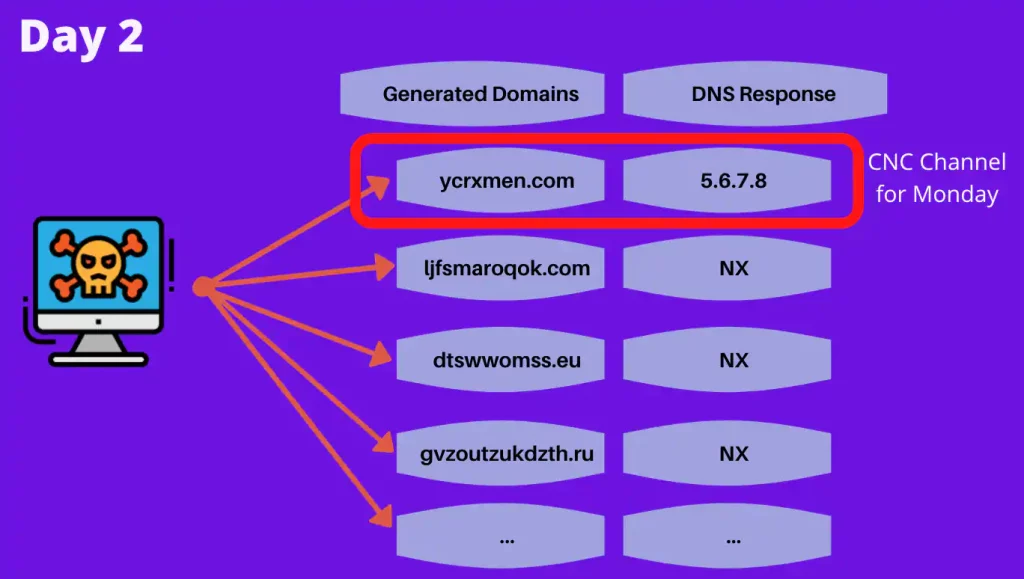
Image Source: https://www.akamai.com
Detection Techniques for DGA Malware:
Creating effective Domain Generation Algorithm (DGA) malware detection rules is essential for identifying and mitigating this type of malicious activity. Here are some detection rules and guidelines for detecting DGA malware:
- Look for Unusual Domain Names:
- Create rules to flag domain names that are unusually long or appear random. Legitimate domains typically follow recognizable patterns, so detecting irregularities in domain names can be an indicator of DGA usage.
- Regular expressions or string length thresholds can be used to filter out suspicious domains.
- High Query Rate:
- Implement rules that identify systems or IP addresses generating a high volume of DNS queries in a short time frame. DGA malware often generates numerous DNS queries to resolve its generated domains.
- Set threshold values to trigger alerts for abnormally high DNS query rates.
- Non-Existent or Invalid Top-Level Domains (TLDs):
- DGA-generated domains often use invalid or uncommon TLDs. Create rules to detect DNS requests for domains with TLDs that don’t match a list of valid TLDs.
- Alert on DNS requests to TLDs like “.local,” “.invalid,” or other non-standard TLDs.
- Domain Fluxing Patterns:
- Some DGA algorithms exhibit specific patterns in the generated domains. Analyze historical DNS data to identify recurring patterns and create detection rules that trigger alerts when these patterns are observed.
- Regular expressions and pattern matching can be useful for identifying such recurring patterns.
- Multiple DNS Query Failures:
- Look for systems that repeatedly query non-existent or unresponsive domains. DGA-generated domains may often result in DNS query failures.
- Set thresholds to trigger alerts when a system makes an unusually high number of failed DNS queries.
- Geographic Anomalies:
- Analyze the geographic locations of DNS queries. If DGA malware is communicating with C2 servers, it may involve querying domains with IP addresses in a different geographic region than the organization’s typical traffic.
- Create rules that trigger alerts for unusual geographic patterns in DNS queries.
- Zero-Length Response Domains:
- DGA malware may use zero-length responses as a way to indicate C2 communication. Detect and alert on DNS responses that have no data or empty response packets.
- Temporal Analysis:
- Analyze DNS query patterns over time to identify domains that change rapidly, indicating DGA behavior. Set up alerts for domains with short lifespans or frequent changes.
- Machine Learning and Anomaly Detection:
- Implement machine learning models and anomaly detection techniques to identify patterns indicative of DGA usage. Train these models on historical DNS data to detect deviations from normal behavior.
- Honeypots and Sinkholes:
- Deploy honeypots or sinkholes to attract DGA malware and monitor the DNS queries made to these deceptive domains.
- Analyze the DNS traffic to identify infected systems within your network.
- Threat Intelligence Feeds:
- Utilize threat intelligence feeds to keep your detection rules up to date with known DGA indicators and patterns.
- Combine Multiple Indicators:
- Combine several indicators and detection rules to increase accuracy. For example, you can combine high query rates, unusual domain patterns, and geographic anomalies to create a more comprehensive rule.
- Alert and Investigate:
- When a rule is triggered, ensure that it leads to a thorough investigation to confirm the presence of DGA malware and its associated activities.
Remember that DGA malware evolves, and attackers regularly update their techniques to avoid detection. Therefore, it’s essential to continuously refine and update your detection rules and stay informed about emerging DGA patterns and indicators.