What is Slowloris Attack?
Slowloris is a DDoS attack software created by Robert “RSnake” Hansen. The software allows a single computer to take on a web server. The attack’s simple but elegant nature means it does not require much bandwidth to carry out its attack on the server of the target webserver with minimal or no side effect on other ports and services. Slowloris DDoS attack has been demonstrated to be highly-effective against many famous types of webserver software such as Apache 1.x and 2.x.

How Slowloris Attack works?
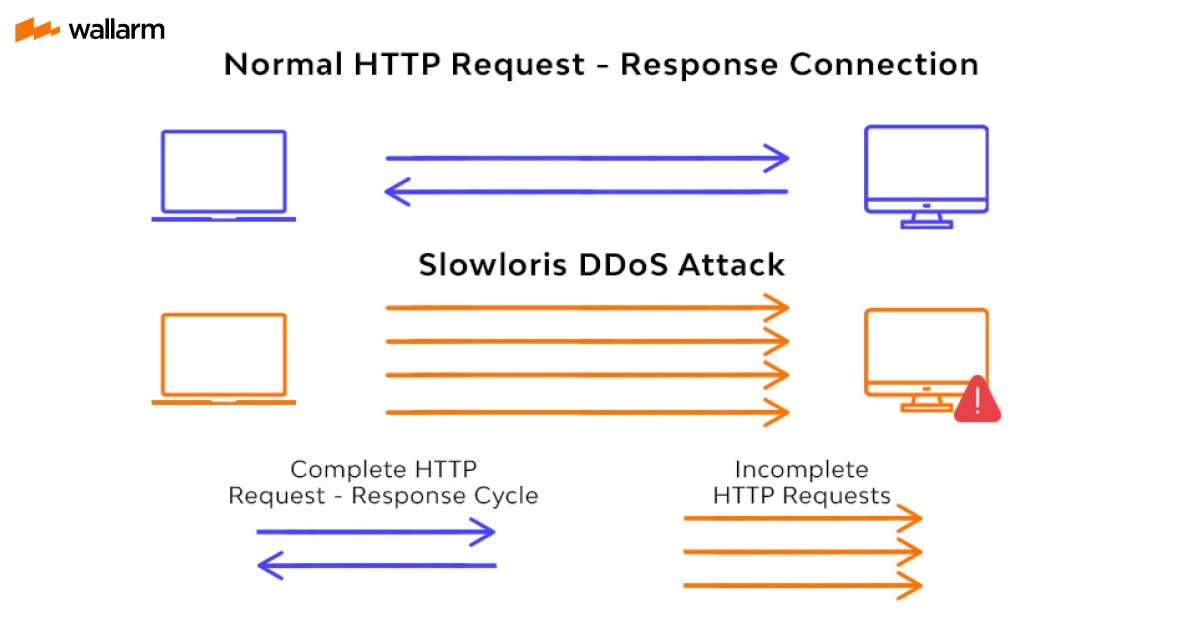
Slowloris operates by opening different connections to the targeted web server and leaving them open as long as needed. It does this by sending partial HTTP requests nonstop, with none completed. The servers that are attacked open further and connectivity open, waiting for the completion of each attack request.
At some intervals, the Slowloris sends successive HTTP headers for every request, but never actually finishes the request. Eventually, the targeted server’s highest simultaneous connection pool gets filled, and extra connection attempts are denied.
By sending incomplete, instead of malformed packets, Slowloris can conveniently slip by conventional Intrusion Detection systems.
Getting its name from a type of slow-moving Asian primate, Slowloris gets the job done by moving slowly but steadily. A Slowloris attack has to wait for the release of sockets by legitimate requests before consuming them one after the other.
For a website with a high volume, it may take some time. The process can be further delayed if legitimate sessions are initiated again. But at the end of the day, if the attack is unresolved, Slowloris—though slow like a tortoise—will eventually win the race.
If unmitigated or undetected, Slowloris attacks can also go on for long periods. When attacked sockets time out, Slowloris usually initiates the connections again, continuing to overwhelm the webserver until it is resolved.
Made for stealth and efficacy, Slowloris can be redesigned to send different host headers if a virtual host is a target, and logs are kept separately for every virtual host.
More importantly, during an attack, Slowloris can be configured to suppress the creation of a log file. The implication of this is that the attack can get unmonitored servers off-guard, without any red flags appearing in the entries of the log file.
A Slowloris attack takes place in 4 steps:
- First, the attacker opens several different connections to the server targeted server by sending multiple incomplete HTTP request headers.
- The target then opens a thread for every incoming request, to close the thread the moment the connection is completed. To work efficiently, if a connection is taking too long, the server will timeout the excessive long connection, freeing up the thread for the next request.
- To prevent the timing out of the target from the connections, the attacker intermittently sends partial request headers to the target to keep the request alive. That is, “I’m still here, though slow. Wait for me please.”
- The server targeted is never able to release any of the open incomplete connections while waiting for the ending of the request. The moment all available threads are being used, the server will not be able to respond to extra requests made from regular traffic, leading to denial-of-service.
The distinguishing attribute of Slowloris is its ability to cause a lot of damage while consuming very little bandwidth.
Why Slowloris attacks are very dangerous and effective.
Slowloris software is developed for efficiency and stealth, and it plays the ‘slow and low’ game. It waits for the release of sockets by legitimate requests and consumes them one after the other, even when it is a high-volume website/web application. The attack can be mitigated in the case of high-volume websites, only if their early detection and legitimate sessions are reinitiated.
Unlike other types of DDoS attacks that send malformed packets or malicious content, Slowloris sends incomplete HTTP requests which allow it to escape conventional scanners and detection systems.
As stated earlier, it does not cost the attackers much as Slowloris attacks utilize minimal bandwidth. This makes it possible for a single computer to bring down a whole high-profile server. As a result, the software has become the go-to tool for hacktivism.
Slowloris software can be manipulated to send different host headers and separately keep logs for each of the hosts if the target is a virtual host.
The software is capable of suppressing the creation of a log file during an attack which makes it possible to catch unmonitored webservers off-guard and slip past without creating red flags in the entries of the log file.
How and why DDoS attacks are launched?
There are different reasons why DDoS attacks are launched. The gaming industry online has been a regular victim of DDoS attacks for a while. Also, there are DDoS for hire services that take on the rival’s website intending to bring it down.
Sometimes, political agendas are the reasons behind the attacks. Good examples of this are Georgia and Estonia that were targeted in 2007. Also, a traffic overload brought down all the media and government websites by Russian nationalists to show their dissatisfaction with the relocation of a Soviet war monument. In 2008, Georgian websites experienced DDoS attacks before the Russian invaded South Ossetia.
Cybercriminals have begun to use DDoS attacks as a disguise to get the attention of businesses away from more dangerous security breaches. DDoS is used as a distraction to target another vulnerability. In such attacks, what would seem like multiple different attacks are launched on the target by the attacker.
Hackers have made it a sophisticated way of diverting attention to disguise other attacks. Most times, financial services organizations that take care of a vast amount of data are easy targets of such attacks.
IT administrators have been at the receiving end of phishing attacks in several European banks lately. Malware is launched to go into the bank systems and steal their login credentials. As soon as the hackers get the login details, they launch DDoS attacks on the bank and keep them busy dealing with it. This gives them time to clone private data and cart it away with the money.
That’s not the only way cybercriminals use DDoS attacks. IP cameras, home routers, and other IoT devices infected with malware can be used to launch DDoS attacks too. Attackers have begun doing the same with Android devices. They use malicious apps on the Google Play store and other third-party stores for this purpose.
A security team from Team Cymru, RiskIQ, Akamai, Cloudflare, and Flashpoint conducted joint research and found a large botnet built of over 100,000 Android devices located in more than 100 countries. The findings took place as a result of massive DDoS attacks that hit various content delivery providers and networks. The particular Android botnet (WireX) was used for sending tens of thousands of HTTP requests. These requests looked like they came from legitimate browsers.
Usually, the goal of launching such attacks is to flood servers with bogus traffic and use their internet RAM, Android, or CPU so that they can no longer serve users' requests. There could be some unknown motive behind it too.
As the applications infected request the device administrator permissions while installing, they let them launch a background service and participate in the DDoS attacks even if these apps are not actively used or when the device has been locked.
DDoS are mass-scale attacks and their victims are usually giant corporate organizations and governments of various states. However, there are consumer-level products too, that can pretty much replicate the work of hackers but on a smaller or individual scale. Spying apps, such as TrackmyFone, Xnspy, etc. are among the known names associated with anything remotely like mobile spying or mobile hacking. When these are secretly installed on a phone, they can allow a third person to remotely access all the data saved on the device. It cannot be compared to a DDoS attack but instead the malware that’s been used to launch a DDoS attack.
Other DDoS attacks types
Some of the most commonly used DDoS attack types are:
UDP Flood
A UDP flood refers to any DDoS attack that floods a target with what is known as User Datagram Protocol (UDP) packets. The attack aims to flood random ports on a remote host. This makes the host repeatedly check for the application listening at that port and (when no application is found) send a response with an ICMP ‘Destination Unreachable’ packet. This process saps host resources, which can eventually lead to inaccessibility.

ICMP (Ping) Flood
Similar to the UDP flood attack, an ICMP flood overwhelms the target resource with what is known as ICMP Echo Request (ping) packets, generally sending packets as fast as possible without awaiting replies. This type of attack can consume both incoming and outgoing bandwidth, since the victim’s servers will often make attempts to respond with ICMP Echo Reply packets, leading to a significant overall system slowdown.
%20Flood%20attack.jpg)
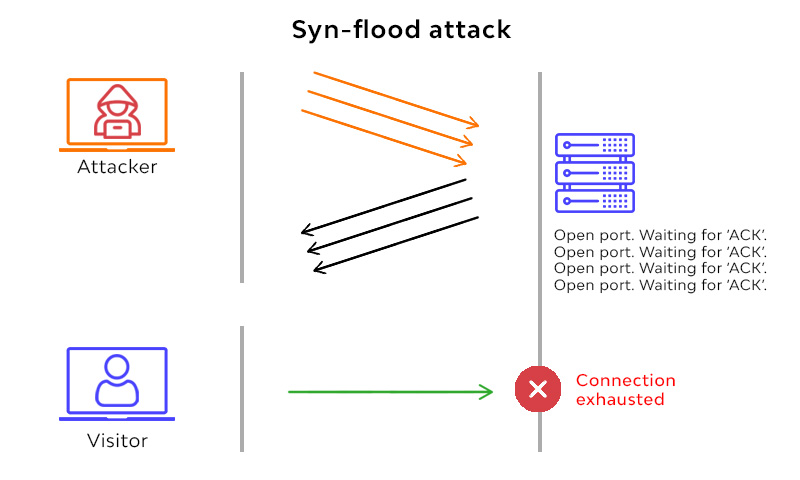
SYN Flood
An SYN flood DDoS attack exploits a popular weakness in the connection sequence of the TCP (the “three-way handshake”), wherein an SYN’s request to initiate a TCP connection to a host must be responded to by an SYN-ACK response from such host, and then confirmed by an ACK reply from the requester. In the scenario of an SYN flood, the requester will send several SYN requests, but will either not respond to the host’s SYN-ACK response or will send the SYN requests from a spoofed IP address. Whichever way, the host system continues to await the acknowledgment of each of the requests, binding resources until new connections can’t be made, and ultimately leading to a denial of service.
Ping of Death
POD or ping of death attack involves the attacker sending several malicious or malformed pings to a computer. The highest packet length of an IP packet (including the header) is 65,535 bytes. However, the Data Link Layer often poses limits to the highest frame size – for instance, 1500 bytes on an Ethernet network. In this case, a large IP packet is split across different IP packets (fragments), and the recipient host reassembles the IP fragments into a full packet.
In the scenario of a Ping of Death, the recipient is left with an IP packet that is bigger than 65,535 bytes when reassembled, following malicious manipulation of fragment content. This can exceed memory buffers assigned for the packet, causing a denial of service for legitimate packets.

NTP Amplification
In NTP amplification attacks, the attacker exploits publicly accessible Network Time Protocol (NTP) servers to overwhelm a target server with UDP traffic. The attack is described as an amplification assault because the query-to-response ratio in such scenarios ranges between 1:20 and 1:200 or more. This means that any attacker that gets a list of open NTP servers (e.g., by using tool like Metasploit or data from the Open NTP Project) can easily produce a devastating high-volume, high-bandwidth, DDoS attack.

In this type of DDoS attack, the perpetrator takes advantage of seemingly legitimate HTTP GET or POST requests to attack an application or web server. HTTP floods do not utilize spoofing, malformed packets, or reflection techniques, and require smaller bandwidth than other attacks to bring down the targeted server or site. The attack is even more effective when it forces the application or server to allocate the highest resources possible in response to every single request.

Zero-day DDoS Attacks
The “Zero-day” involves all unknown or new attacks, taking advantage of the vulnerabilities that no patch has not yet been released for. It is well-known among the hacker community, where the practice of trading zero-day vulnerabilities is now popular.
Slowloris DDoS attack mitigation methods
Here are some of the best known way to avoid slowloris DDoS attacks and mitigation strategies
- Purchase more Bandwidth
The first step you have to take, to prevent a DDoS attack and make your infrastructure DDoS resistant, is to ensure that you have enough bandwidth to take care of any spikes in traffic that could be caused due to malicious activity.
In the past, it was possible to avoid DDoS attacks by ensuring that you had an additional bandwidth compared to any attacker. With amplification attacks becoming more popular though, this is no longer effective. Having more bandwidth raises the bar and the attackers have to overcome before carrying a successful DDoS attack. It is a safety measure, but not a DDoS attack solution.
- Network Hardware Configuration against DDoS attacks
Some really simple hardware configuration changes could help you with preventing a DDoS attack. For instance, if you configure your router or firewall to drop DNS responses from outside your network or drop incoming ICMP packets, this could help you to an extent in preventing certain DNS and ping-based volumetric attacks.
- Protect DNS Servers
Attackers can bring down your website and web servers offline by attacking your DNS servers. So, make sure that your DNS servers have redundancy. DNS is like a phone book for the internet. It matches the website name of the user seeking the correct IP address. There are more than 300 million domain names keeping millions of internet users around the world connected. The internet wouldn’t work without it. That’s why it is a critical target for attackers. The DDoS attack on your DNS infrastructure could render your application or website to be completely unreachable. So, network operators need to adequately defend their DNS infrastructure to protect it from DDoS attacks.
Other than this, spread your servers across various multiple data centers if you want to give the attackers a really hard time successfully launching a DDoS attack against your servers. You can make these data centers in different countries or at least in different regions of the same country. If you want this strategy to turn out well, all the data centers must be connected to different networks, and no network bottlenecks exist or single points of failure on these networks. When you distribute your servers geographically as well as topographically, it makes it hard for an attacker to successfully attack more than a part of your servers. Also, it would leave other servers unaffected and enable them to bear some of the extra traffic the affected servers would handle normally.
- Transparent Mitigation
Hackers could be launching the DDos to make your users lose access to your site. When your site is under attack, you must use a mitigation technology to enable people to continue using it without making it unavailable and without making them see splash screens and outdated cached content. Once the hacker sees that you are not being affected by the attack and your users are still able to access the site, he might stop and not return.
- Anti-DDoS hardware and software modules
Along with having your server protected by network firewalls and other specialized web application firewalls, you must use load balancers. You can also add software modules to another webserver software for DDoS prevention. For instance, Apache 2.2.15 ships with a mod_reqtimeout that protects you against application-layer attacks like Slowloris. They keep the connections to a web server open as long as possible by sending out partial requests till the server is rendered unable to accept any request for new connections.
You could also use hardware modules that come with software protection against DDoS protocol attacks such as the SYN flood attack. This could be done by monitoring how many incomplete connections exist and then you can flush them as the number reaches a configurable threshold value.
FAQ
References
Subscribe for the latest news