IDS is the system which is monitoring the traffic in the network. This will generate alerts for any of the suspicious activity when discovered in the network. Anomaly detection and reporting are the main functions. Some of the intrusion detection systems are still capable of taking actions when any malicious activity is detected. It also includes the blocking of the traffic when it is sent from any Internet protocol addresses.
IDS can be contrasted with the Intrusion prevention system (IPS) which is monitoring the packets on the network which are damaging the traffic on the network. Like IDS its primary function is to prevent the threats when it is detected. This is opposed to the recording and detecting the threats.
How Intrusion Detection Systems would work?
IDS are mostly used for detecting anomalies with the aim of catching the hackers before they do any real damage to the network. They can be either host-based or network-based. Host-based IDS are installed on the client computer while the Network based ids protection are residing in the network.
IDS are working either with the signatures of the attacks or it is deviating from the normal activity. These anomalies and the deviations are pushing up the stack when examining the protocol and the application layer. They are detecting the events like Christmas tree scans and the DNS positionings.
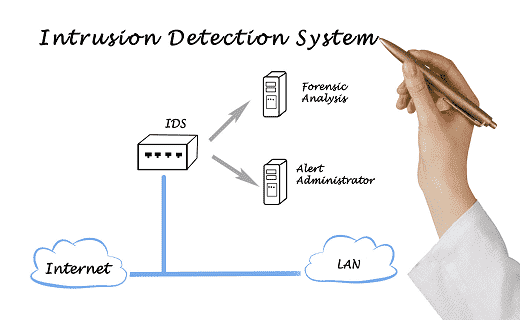
Intrusion detection systems work by either looking for signatures of known attacks or deviations from normal activity. These deviations or anomalies are pushed up the stack and examined at the protocol and application layer. They can effectively detect events such as Christmas tree scans and domain name system (DNS) poisonings.
You can implement an ids protection as a software application that runs on your customer hardware or it can be run as a network security appliance too. There are intrusion detection systems that are cloud-based and are available to protect systems and data in cloud deployments.
Different types of IDS systems:
Like other systems, IDS systems also come in multiple flavors and have different capabilities to detect any threats or suspicious activities using multiple methods including these:
NIDS system:
This is a network intrusion detection system and is deployed at points or points which are strategic within your business network. At these points, it can monitor the outbound and inbound traffic from and to all the network devices.HIDS system:
this is a host intrusion detection system that runs on all the devices or computers that are in the network and gives direct access to both the enterprise’s internal network as well as the internet. There is quite an advantage of using a HIDS instead of NIDS because it has the capability to detect network packets that are anomalous and originate from within the organization and even that malicious traffic or activity that is not being detected by a NIDS system. A HIDS also has the capability to identify traffic that is malicious and originates from the host, such as when there is an infection in the host with malware and it is attempting to get spread to multiple systems.SIDS system:
This is a signature-based system for intrusion detection that is capable of monitoring all packets that traverse through the network and compares them with the database of attributes of malicious threats that are known or of attack signatures much like the working of antivirus software.AIDS system:
This is known as the anomaly-based system of intrusion detection that is known to monitor the traffic over the network and compares it with respect to an established baseline in order to determine what should be considered as normal activity in the network with respect to protocols, bandwidth, other devices, and ports. This type of IDS system makes use of machine learning in order to establish one baseline and also its accompanying policy for security. When the system identifies any sort of policy violations or suspicious activity then the alert is sent to the IT teams. By detecting these threats by making use of a broad model instead of specific attributes and signatures the IDS system is anomaly-based works to improve upon the limitations that are found in signature-based methods especially when they are detecting the novel threats.
Historically the categorization of IDS systems was done as active or passive. A passive IDS system can detect suspicious activity and would generate log entries or alerts but will not take any action. On the other hand, an active IDS system also known as IDPS works by generating alerts as well as log entries and it can be configured to take requisite actions in case of threats like shutting down access or blocking IP addresses to restricted resources.
Related Resources: